Resilient Cyber Newsletter #61
- Chris Hughes from Resilient Cyber <resilientcyber+resilient-cyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
Resilient Cyber Newsletter #61Security Budget Declines, Cyber Funding Snapshots, AI Bubble, State of AI 2025, Vulnerability Scoring & GRC Engineering Learning HubWelcome!Welcome to Issue #61 of the Resilient Cyber Newsletter. School year is or soon will be upon us, and for those working from home like me, it is a bittersweet time. On one hand, you’re sad to see the kids go back to school, and on the other, you can begin to at least hear yourself think amongst the backdrop of kids being kids! Personal stuff aside, I’m excited about this issue. We have a lot of great content to explore this week, including the state of security budgets, AI, and deep dives into vulnerability scoring, so let’s get started. Interested in sponsoring an issue of Resilient Cyber? This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives Reach out below!
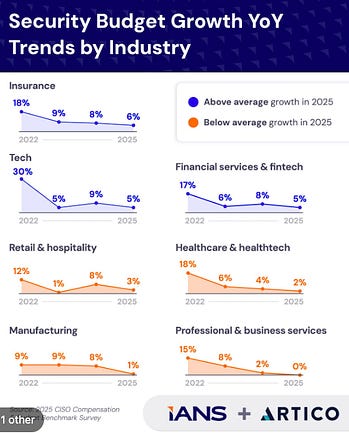
Cybersecurity Leadership & Market DynamicsSecurity Budget Growth (Decline) YoY Trends by IndustryIANS and Artico Search recently conducted a Budget Benchmark Report, which supports many of the pain many have been feeling in cyber. While many quip that cybersecurity is immune and insulated from broader economic headwinds or challenges, as it turns out, that isn’t always the case. Their survey showed that security budget growth is declining or flat in some sectors YoY from 2022-2025. This is likely due to broader economic challenges, but also more scrutiny of security budgets, leadership emphasis on Return on Security Investment (ROSI), and the push for consolidation and to get a handle on security tool sprawl that is driving the platformization push in the industry that Palo Alto Networks and others are making. Cybersecurity Funding SnapshotI continue to follow Matthew Ball of Canalys because he routinely shares excellent insights on the cyber ecosystem from a market perspective. He recently shared the image below along with some helpful insights. Matt covered key points, such as:
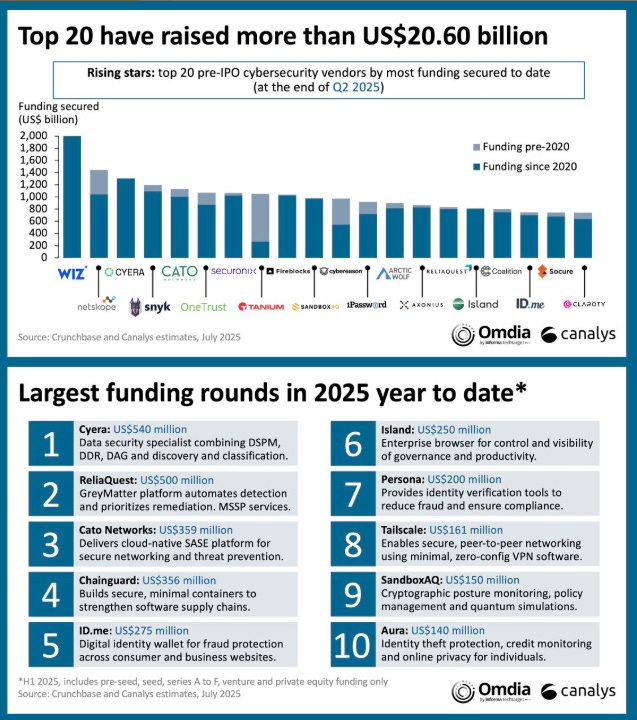
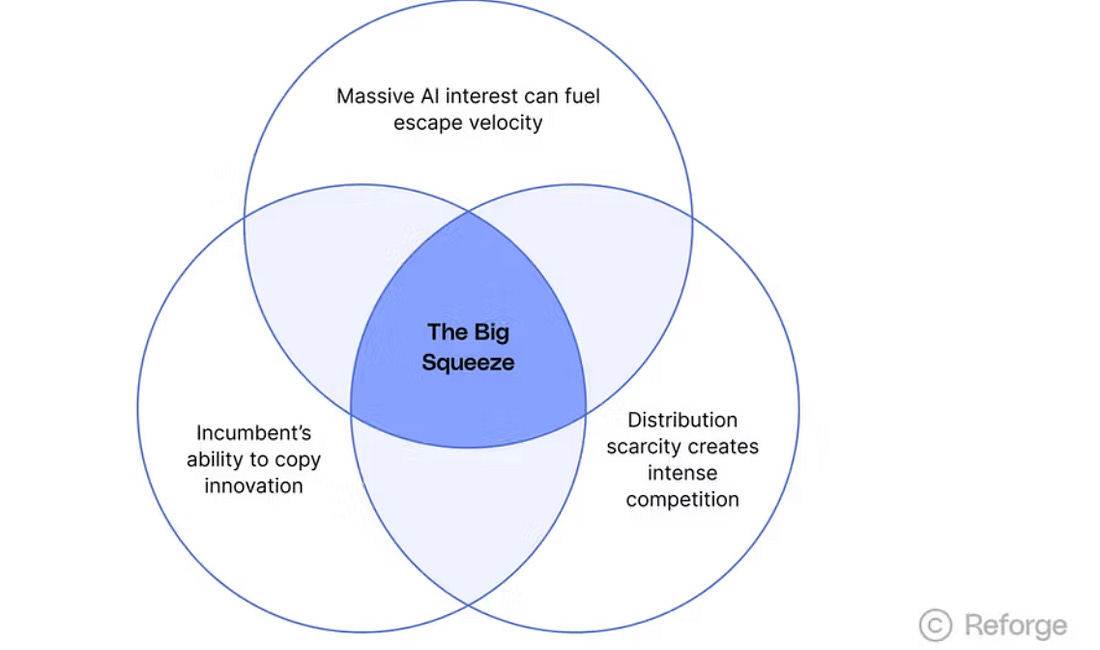
Cyber Funding Snapshot and Funding RoundsSpeaking of Canalys, Jay McBain, who works with Matthew, whom I cited above, also shared some great insights recently. This includes the fact that the Top 20 pre-IPO cyber companies have raised more than $20.60 billion this year (end of Q2 2025). The largest funding rounds involve leaders such as Cyera, Chainguard, Island, and others. Jay points out that 73% of the funding was by US-headquartered firms, followed by 14% from Israel. Competitive Advantage Through Cybersecurity: A Board-Level PerspectiveThis piece from McKinsey and NACD captured insights from five industry-leading CISOs and board directors about how cybersecurity is changing and how CISOs and Directors can use their position and influence to drive competitive advantage through cybersecurity. The CISOs being interviewed discuss the challenges of dealing with diverse boards, many of whom have financial and business backgrounds rather than technology backgrounds. They also share insights on how they prepare for board meetings and position cyber issues for input and awareness. The interview provides valuable perspectives from existing CISOs and board members and is worth reading for those looking to understand better how they can communicate cyber issues to the board. Why Escape Velocity Is More Important Than EverThis piece from Reforge also discusses the need to achieve accelerated ARR and broader revenue goals. It opens by discussing how Lovable hit $100M ARR in just 8 months from launch, outpacing traditional metrics, even for outstanding industry-leading firms. Many rapidly growing firms focus on “Vibe Coding” or supporting development workflows more broadly, including examples such as Glean, Cursor, and Codium. These firms hit the Development Platform and Tooling aspect of the previous piece I shared from Bessemer. Using Lovable as an example, the author discusses how they have navigated three distinct market trends:
This includes riding the wave of AI hype, incumbents copying innovators, and a distribution scarcity creating intense competition. They argue that this is causing startups to need to get massive distribution quickly to reach “escape velocity” and stay on a trajectory to be lasting industry leaders. As the author notes, speed cuts both ways, though. Just as quickly as an innovator can get breakout velocity, incumbents can copy them. While the piece isn’t about cybersecurity, many of the same principles apply to the cybersecurity startup and incumbent landscape. Yes, AI is in a BubbleAt least according to OpenAI CEO Sam Altman. Sam recently discussed that investors are overexcited about AI and compared the current market fervor to the 1990s during the dot-com bubble, which, as we all know, was eventually followed by an associated crash. Sam cited the small team sizes, high valuations, and abnormally large funding rounds as evidence of the current market hype around AI. He even went on to say:
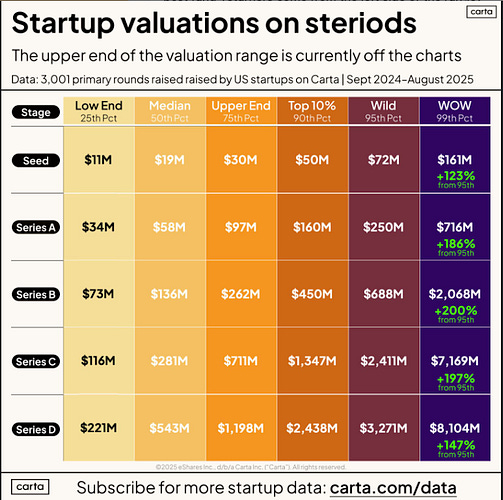
Continuing the interview, Sam said he expects OpenAI to survive the forthcoming burst and that they intend to spend trillions on data center construction soon. Sam’s comments reminded me of recent comments from Peter Walker, Head of Insights at Carta, whom I regularly follow. Peter recently stated:
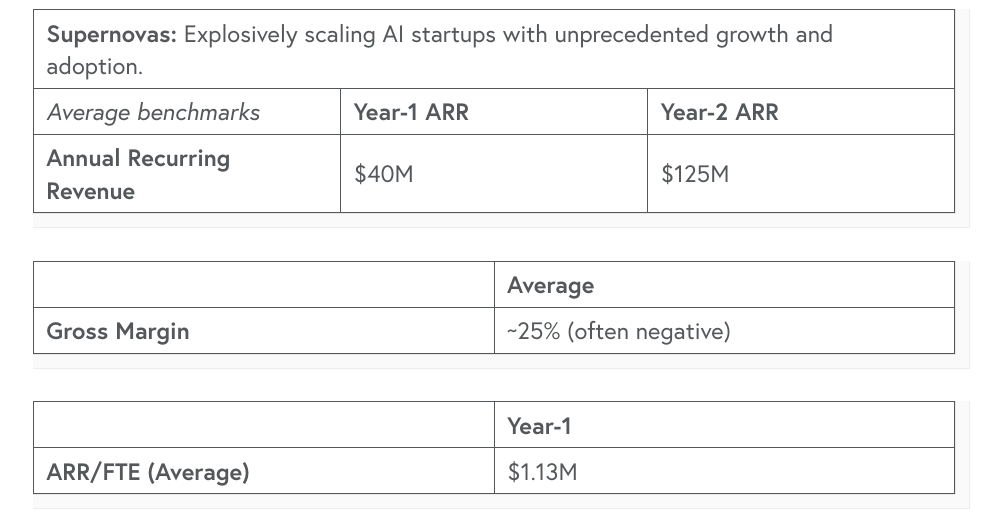
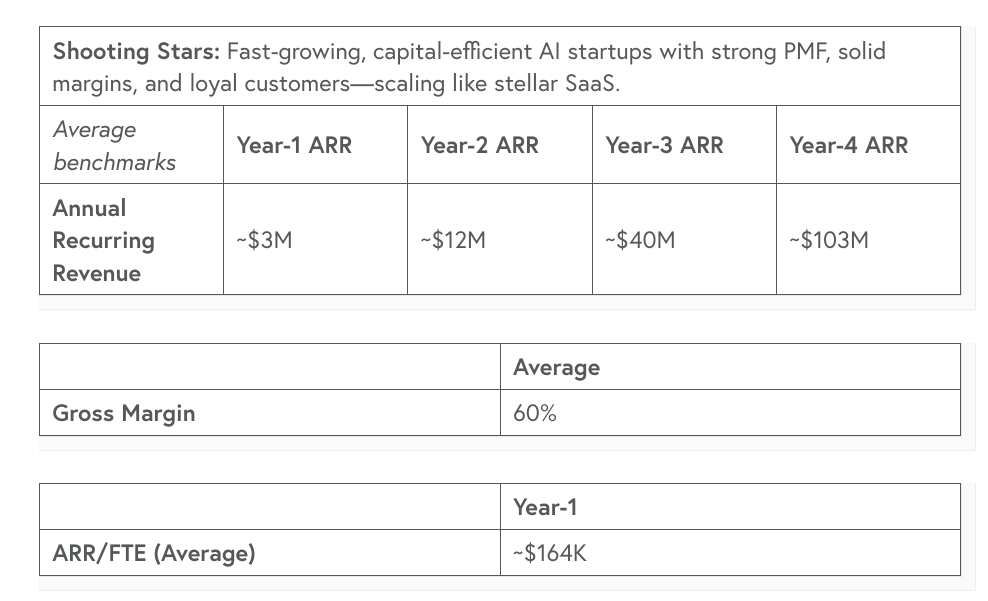
Peter shared the below image, stating medium figures in every stage are higher than they were last year and rival all-time peak values and points out in some cases (such as the WOW column) we are in a new peak bubble that even makes 2021 look weak. AIThe State of AI 2025AI, of course, is dominating headlines, including everything from venture capital to cybersecurity. That is why it was great to check out this State of AI Report from Bessemer Venture Partners (BVP). As the report discusses, we’re moving past AI's initial big bang and starting to get a stable sense of the ecosystem, including foundational companies, best practices for building, and patterns for startup success. One of the biggest takeaways from the report is how AI has redefined what “good” looks like from a metrics and benchmark perspective, no longer aligning with benchmarks from the SaaS era. Since 2023, Bessemer has deployed over $1 billion in capital to AI-native startups. Not only are countless AI-native startups forming, but every established SaaS company is now weaving AI capabilities into its products as well. Below are examples of new benchmarks when it comes to AI-native startups: They draw distinctions between what they dub “supernovas” and “shooting stars,” showing the wide range and disparities among AI-native startups. Some achieve unheard-of, rampant, accelerated growth, while others achieve substantial growth by traditional standards. Despite the rapid ARR growth, the report does highlight how tight margins are, being close to zero or even negative in some cases, and we have seen some highlight this with memes, including inference costs, etc. The report provides some insights into the average gross margins of the supernovas, as listed below: They discussed how AI “Shooting Stars” more closely resemble traditional SaaS companies, with quick PMF and customer retention/expansion, but not as insane initial ARR’s. While it could be tempting for founders to hyperfocus on supernovas, Bessemer argues that the shooting stars will include hundreds of new startups, which is what AI founders should aim for. The report then discusses a roadmap for the AI cosmos, including AI infrastructure, developer platforms and tooling, horizontal and enterprise AI, vertical AI, and consumer AI. It also lays out five key predictions. Resilient Cyber w/ Andrew Carney DARPA AI Cyber Challenge AIxCCIn this episode, I interview Andrew Carney, the Program Manager for DARPA's AI Cyber Challenge (AIxCC). Listen on:
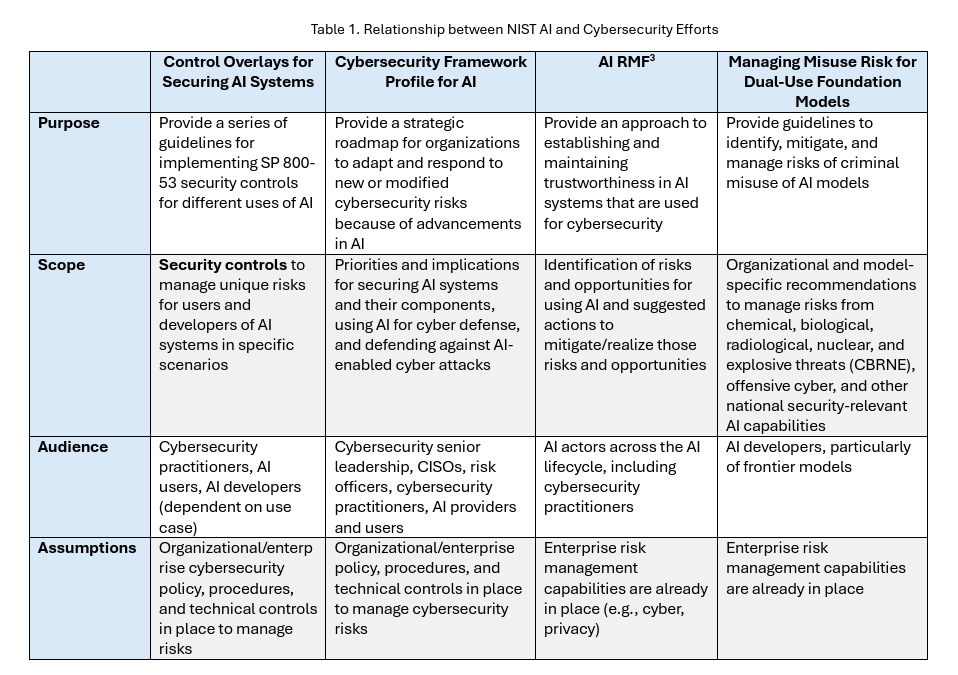
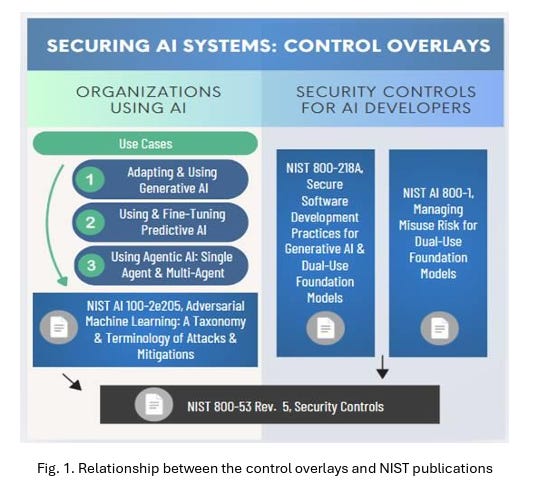
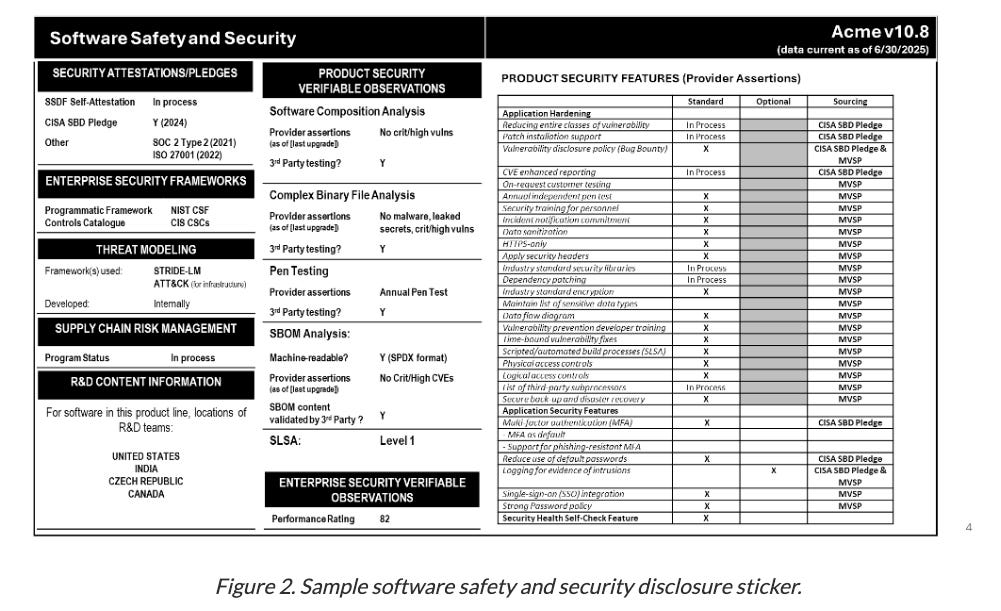
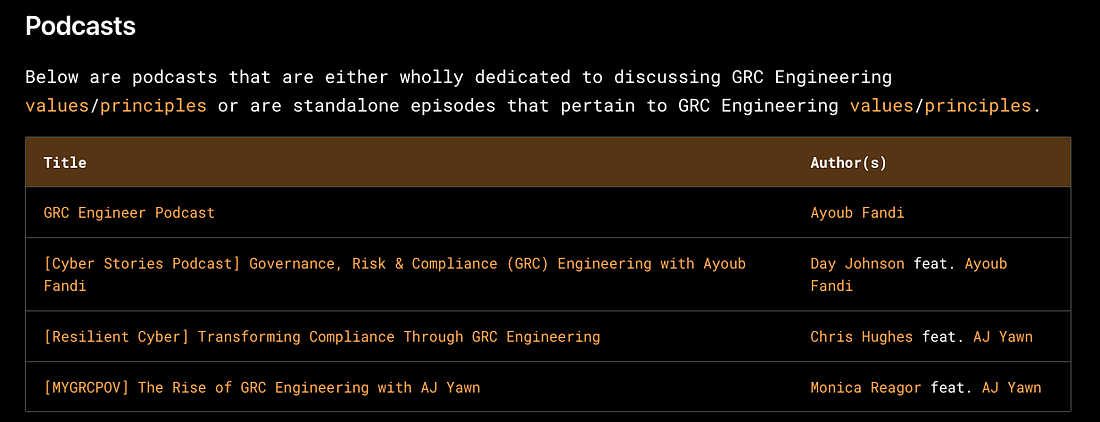
 NIST to Release Security Control Overlay for Securing AI SystemsNIST recently released a concept paper and announced that it will release a security control overlay for securing AI systems for its NIST 800-53 security control catalog, which underpins many popular compliance frameworks, such as FedRAMP, RMF, CSF, and more. They laid out how the 800-53 AI Security Control Overlay intercedes with other related NIST AI efforts such as the AI RMF and others below: In short, the overlays aim to provide security controls to manage unique risks for users and developers of AI systems in specific scenarios. They also envision it being able to be used by both organizations using AI, as well as developers of systems involving AI: AppSec, Vulnerability Management & Software Supply ChainConflicting Scores, Confusing Signals: An Empirical Study of Vulnerability Scoring SystemsThe more time I spend in this field, the more I believe that Vulnerability Scoring systems are all flawed, imperfect, and just one indicator to drive vulnerability prioritization. Zero Trust is a BustOr, at least the leading ZT tools are. That was one of the key points recently made at DEFCON. While ZT has been a trend and term cyber marketing teams have clung to for years, researchers have shown that the leading ZT vendors/tools are rife with vulnerabilities and weaknesses. They found Checkpoints' product had hard-coded encryption keys, which exposed customer data, Zscaler’s SAML implementation failed to validate signatures, and Netskope suffered from cross-tenant vulnerabilities, letting attackers compromise any organization using leaked enrollment keys. All of these examples violate fundamental tenets of ZT. This also aligns with an article I wrote recently, calling out the uncomfortable truth that “Your Security Tools May Be Making You Insecure”. In the piece, I spoke about the fact that many security tools are vulnerable and often shelfware, not fully implemented, configured, tuned or used - leaving organizations more vulnerable as these products sit around with elevated permissions and access. A “Window Sticker” for SoftwareWe’ve heard a lot about software supply chain security in the last several years, since the fallout of events such as Log4j, SolarWinds, and others, as well as the Federal Executive Order (EO), which placed a large emphasis on supply chain security. This piece from Lawfare discusses the concept of a “Window Sticker” for software, and how buyers can use performance measures to drive better security in software products. The above image exemplifies what the proposed sticker “could” include, citing examples of compliance alignment, CISA’s SbD pledge, SCA results, product security features, etc. While on the surface, this is a well-intentioned concept and not a new one, and I like the idea of trying to drive consumers to force vendors to create more security products, the reality is much more nuanced than this. Most consumers understand little of what this image shows, and more importantly, they know that there is a significant amount of nuance and details this image can’t reflect. CISA SbD signatories such as Fortinet and others routinely drop news of their products being exploited by zero days. SBOMs have lingering challenges around completeness, correctness, and quality. Not all SCA “Criticals” and “Highs” reflect real-world risk when aligning with CVSS, and much more. Due to these complexities and the fact that consumers often want the cheapest, not the most secure products, I don’t anticipate this vision becoming a reality anytime soon. GRC Engineering Learning HubYou’ve heard me talk a lot about GRC Engineering, and the crew that released the GRC Engineering Manifesto recently released a Learning Hub. This includes, books, courses, labs and podcasts on the topic. I was pleasantly surprised to see my own conversation with my friend AJ Yawn’s conversation listed among the podcasts. It also lists a lot of helpful blogs, newsletters and talks and interviews. The learning hub is worth bookmarking and referencing for those interested in GRC Engineering. Invite your friends and earn rewardsIf you enjoy Resilient Cyber, share it with your friends and earn rewards when they subscribe. |
Similar newsletters
There are other similar shared emails that you might be interested in: