Resilient Cyber Newsletter #37
- Chris Hughes from Resilient Cyber <resilientcyber+resilient-cyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
Resilient Cyber Newsletter #37Cyber Market Analysis Themes, Russia Cyber Planning, Hacking AI Agents/Apps, LLM Exploit Generation, & Runaway CVE Growth and PrioritizationWelcome!Welcome to another issue of the Resilient Cyber Newsletter. This week, we cover a broad range of topics, from a 2024 cybersecurity market analysis looking at funding and M&A trends to a look forward to the rest of 2025. We dive into AI from Rise of Agentic AI, LLM Exploit Generation, and Runaway CVE Growth and Prioritization Challenges. So, kick back and enjoy the discussions, resources, and topics this week! On a personal note, I got a physical copy of my book that focuses on software supply chain security, “Software Transparency: Supply Chain Security in an Era of a Software-Driven Society”, last week in Japanese, as it has resonated not only in the U.S. market but now is on the shelves in Japan, which is incredible and more than I ever anticipated accomplishing. Interested in sponsoring an issue of Resilient Cyber? This includes reaching over 30,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives Reach out below!
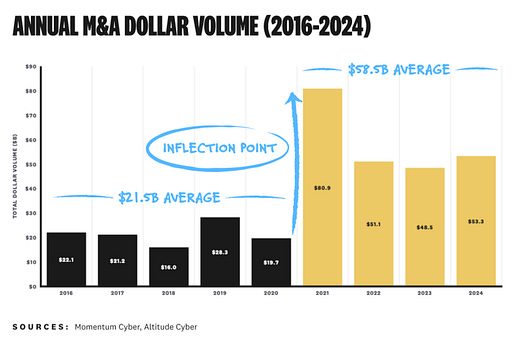
Cyber Leadership & Market DynamicsLatest DOGE Order Aims to Cut Costs Through Federal ContractsThe latest order aims to cut costs through federal contracts as DOGE continues to carry out its activities across the U.S. federal ecosystem. This includes increased scrutiny of programs, a focus on removing broad consulting engagements without concrete deliverables/outcomes and also looking to establish a system to track and report on contract spending across each agency. In fact, some firms, such as Booz Allen Hamilton, have already seen negative trends in their share price due to the news. It is reported that BAH generates 98% of its ~11B in annual revenues from contracts with the U.S. government. Similarly, Leidos gets 87% of its revenue from the U.S. government. This demonstrates how some firm’’ concentration of customer base can make them particularly exposed and vulnerable. This is contrasted with other “large” firms in the Federal space, such as Accenture, which obtains only 17% of its North American revenue from the U.S. government. Secure-by-Design DelusionsOver the last several years we have heard a TON about Secure-by-Design. This is in large part due to the amazing work of the talented folks at Cybersecurity and Infrastructure Security Agency. Themes from (and Beyond) the 2024 Cyber MarketFew in the industry do as great of a job looking at the cybersecurity industry as a market as Cole Grolmus. He leads Strategy of Security, and if you aren’t following him, you should be. He recently did a deep dive into Altitude Cyber’s 2024 market review and provides several excellent insights into the 2024 market and where we may be headed in 2025, including:
Below are a couple of the excellent articles in the article as well, which help visualize the analysis: Hegseth Orders Cyber Command to Stand Down on Russia PlanningIn an announcement that has led to much-heated debate within the cyber community, it has been reported that U.S. Defense Secretary Pete Hegseth last week ordered U.S. Cyber Command to cease all planning against Russia, including offensive cyber actions. The move is being pursued as a part of a broader diplomatic effort to end the war in Ukraine. It’s being reported it could impact several thousands of U.S. personnel across various agencies and entities who conduct offensive and defense operations in cyberspace. One of the security peers in my network, Jacob Williams, penned a damning LinkedIn article titled “Stop Tracking Russian Cyber? That’s Not How Anything Works..”. In the article, Jacob lays out several challenging aspects of this latest directive, such as procedural problems when it comes to threat actor tracking and classification, false flag operations that could be disguised as Russian, as well as fostering distrust in Government attribution. Ironically, news also recently revealed that CISA stated they are NOT changing their stance when it comes to detecting and disrupting Russian APTs, despite the recent directive from the Trump administration. Given that, there seems to be some disagreement or disconnection between the DoD and CISA with regard to Cybersecurity and Russia. I suspect this could also be due to the fact that a new Director for CISA hasn’t been named yet, so their viewpoints as an organization may not be entirely in line with the DoD, which has a new Trump-appointed SecDef. “I Tell startups to leave Europe,” says Dutch CEO of tech unicorn RemoteMany tech leaders across Europe continue to raise concerns about overregulation, with the latest warning coming from the CEO of Remote. Job van der Voort recently stated the EU is going “overboard on tech regulation.” Job is the CEO of Remote, which is valued at over $3bn. He discusses how the regulation in the EU is stifling innovation and will have economic ramifications for the EU and companies trying to exist there. We see this trend unfolding while the EU drives ahead with efforts such as NIS2, DORA, the EU AI Act, and more, while the U.S. is conversely pursuing a large deregulatory push with the new U.S. Presidential administration. The Fastest Way to Understand and Communicate the Value of a ProductWhile a product's technical capabilities are key, and engineers and developers know this better than most, they also need to be able to communicate its value, especially early on. Founding teams and early-stage startups spend a fair amount of their time building market and brand awareness, evangelizing their vision, and trying to find product market fit. This is an excellent post from Crystal Poenisch, who has held marketing roles at various successful companies, such as Chainguard and Aqua Security. She discusses how product marketers and founding sales teams need to understand products, what they do, how it does it and the value it brings to prospects and early customers. She covers key topics, such as:
AIHow to Hack AI Agents and ApplicationsThis is a truly awesome article from Joseph Thacker. Even as someone now on the "offensive" side of security, this is incredibly well written and helps you understand how AI agents and AI applications are potentially vulnerable and can be exploited.
LLM Exploit Generation: Claid, DeepSeek, OpenAIThere has been much discussion about whether, how, and to what extent malicious actors can use LLMs to impact and aid exploit activity significantly. That said, there isn't a lot of great research showing how effective in application LLMs can be in exploitation.
The Rise of AI AgentsBy now, you've likely realized that there is a story, post, or article about Agentic AI everywhere you turn. But what the hell is it exactly, and what will its impact be? I found this paper from James Carson to be a great concise primer and deep dive on the topic.
Revolutionizing OffSec: A New Era with Agentic AIAgentic AI is the buzzword of 2025, with startups and incumbents looking to leverage it for everything, including cybersecurity. This covers areas such as SecOps, AppSec, GRC, and, yes, Offensive Security (OffSec). In this piece, Shahar Peled argues that OffSec hasn’t evolved with broader security when it comes to DevOps, APIs, Automation, and more and is still plagued with problems such as being point-in-time, expensive, and challenging to scale. He argues that Agentic AI can change this by moving towards making Pen Testing continuous, context-aware, and actionable. That said, he cautions we aren’t there yet and challenges remain, but their promise is real, which could disrupt Pen Testing as we know it. Defining LLM Red TeamingWe continue to see Red Teaming as a key aspect of secure LLM adoption, from sources such as the EU AI Act to NIST's AI RMF.
How we beat alert fatigue with AIOrganizations continue to explore AI's value in cybersecurity challenges. One of those is alert fatigue, as organizations struggle to keep up with notifications about vulnerabilities, malicious activity, misconfigurations, and more. This is a good blog from Sean Cassidy at Asana, looking at how they leverage AI to address alert fatigue. They are focusing on their SIEM tool and looking to drive down the false positive rate to ensure analysts look at real security risks rather than noise, which leads to cognitive overload and potentially missing real threats. They also use AI to analyze and enrich alerts and actively engage involved users to verify activity and determine whether it is malicious or benign. They are also exploring the use of AI for vulnerability triage, enriching vulnerabilities with custom fields, setting up due dates, and adding comments for analysis by security teams. The team is also exploring additional AI use cases such as auditing access to production, conducting security reviews, bug bounty routing and more. Extracting the GPT4.5 System PromptIf you’ve been learning much about GenAI and LLM security, you know that the system prompt is an enticing target for attackers and something GenAI providers try to safeguard. As it turns out, OpenAI didn’t do such a great job of doing that with their latest release, ChatGPT 4.5. At least, that is the takeaway from a recent blog post from AI security startup Knostic. They demonstrate how they got ChatGPT 4.5 to turn over the system prompt by utilizing well-crafted prompts. If you’re looking to learn more about AI Security, you can catch my conversation with Knostic Co-Founder and industry security legend Sounil Yu below:  AppSec, Vulnerability Management and Software Supply Chain Security (SSCS)Vulnerabilities Continue to ExplodeVulnerability Researcher Jerry Gamblin recently shared a snapshot of the CVE landscape as we head further into 2025, and it’s bleak. We already know organizations struggle to keep up, with vulnerability backlogs ballooning to hundreds of thousands and millions of unresolved vulnerabilities in large enterprise environments. As he shows, we saw 48.37% year-over-year CVE growth in 2025 compared to 2024, and of course, 2024 also saw double-digit growth over the prior year. Has your organization gotten 48% more effective in vulnerability management in the last year? We all know the answer there. Taking an Evidence-Based Approach to Vulnerability PrioritizationAs vulnerabilities continue to balloon out of control and organizations' internal vulnerability backlogs climb in tandem, many are looking for ways to optimize their vulnerability prioritization. This article from my friend Patrick Garrity at VulnCheck provides a good framework for evidence-based vulnerability prioritization. The article also emphasizes that only 1.1% of vulnerabilities over the past decade are known to have been exploited, further illustrating that focusing on exploitation is a key part of effective prioritization. Patrick also discusses the nuances of exploit availability, such as the difference between weaponized exploits, and Proof-of-Concepts (PoC)’s. The chart below also helps demonstrate how exploit maturity builds into known exploitation. Frequently lost in the conversation of prioritization is internal organizational context. Patrick covers factors such as assets being connected to the Internet, remotely reachable, the automatability of exploitation, and more. EPPS is NOT foolproofAs organizations continue to drown in vulnerabilities, the industry has sought improvements to add a signal to the noise. Vulnerability backlogs have ballooned to hundreds of thousands or millions for large enterprise environments. OpenSSF SBOM CatalogWhile many have grown skeptical of Software Bill of Materials (SBOM) and their utility and value, there are also many others who continue to view them as a key part of broader software supply chain security and AppSec efforts. This resource from OpenSSF is a data set of SBOM tools and resources across the two leading SBOM formats, CycloneDX and SPDX respectively, which is interactive and can be used to identify tools, resources and more. Invite your friends and earn rewardsIf you enjoy Resilient Cyber, share it with your friends and earn rewards when they subscribe. |
Similar newsletters
There are other similar shared emails that you might be interested in: