Navigating FedRAMP 20x and Public Sector Compliance
- Chris Hughes from Resilient Cyber <resilientcyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
I recently had the opportunity to join leaders from Chainguard and Second Front Systems to explore all aspects of FedRAMP 20x and broader public sector cybersecurity and compliance. What made the conversation great was that both leaders who joined me on the panel, Quincy Castro and Donnie Hasseltine, brought a wealth of experience spanning roles from the NSA, USMC, Academia, venture capital, and industry-leading commercial tech innovators. This brought a lived experience to the discussion, as we navigated the complexities of public sector cybersecurity and compliance, including those related to FedRAMP, DoD’s SRG Impact Levels (IL), ATO, and RMF. I’ll be breaking down the talk below with my own thoughts and commentary, and if you want to watch it yourself, you can check out the video right here: 
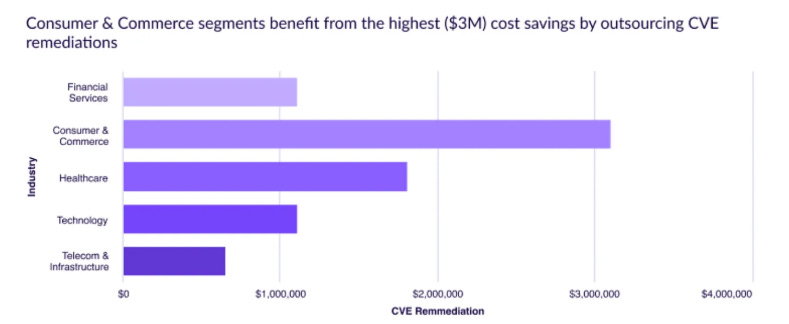
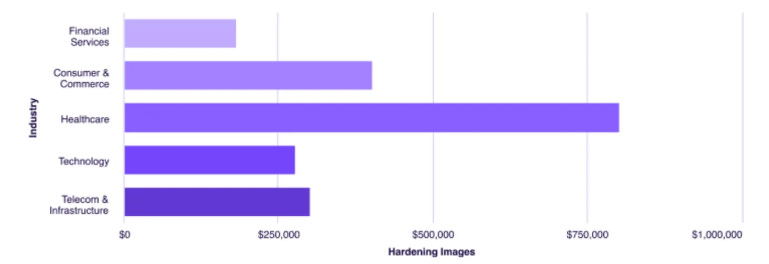
FedRAMP 20xWe began the conversation with a high-level recap of FedRAMP and the FedRAMP 20x initiative. While FedRAMP was initially established to facilitate access for Government agencies and stakeholders to innovative commercial cloud service offerings, ironically, the program originally had the opposite impact. After its first decade in existence, the program had only 350~ authorized cloud services in a market of tens of thousands. As the program continued to receive more scrutiny and draw the ire of public civil servants and commercial partners alike, FedRAMP 20x was introduced to help modernize the program, streamline and rapidly expand authorizations, focusing on key aspects such as automation, machine-readable artifacts, and maximized security control inheritance, among others. What made our session so awesome was that we literally had the FedRAMP Director, Pete Waterman, in the audience, participating in the live Q&A and Comments, providing feedback, clarifying context, and more. We covered a lot of key topics, such as: This includes the shift to context-based vulnerability management, which accounts for aspects such as known exploitation, exploitation probability, reachability, compensating controls, and other relevant factors. While we acknowledged this change was way overdue and brought FedRAMP closer to the latest approaches to vulnerability management from the commercial sector, we also emphasized that this is still not easy, which is why offerings such as Chainguard’s Hardened Images are such a compelling service offering, allowing users to start with CVE-free base images and not inherit significant technical debt right out of the gate when standing up applications and environments. We also spoke about the sheer complexity and challenges of navigating FedRAMP and public sector compliance requirements, which have led many organizations to seek out hardened and authorized platforms such as Second Front Systems Game Warden, which allows for security control inheritance, built-in ATOs/Authorizations, and abstracts away a lot of the compliance and security toil for end users. Security as a Business Enabler In PracticeOne of my favorite themes throughout the conversation was that we discussed what it looks like when we take one of the common buzz phrases in cybersecurity “security from a business enabler” and move it from optics to outcomes. While I don’t work for neither Chainguard nor Second Front Systems, I’ve long known of both of the organizations for exactly this reason. Both organizations have incredible offerings that help abstract away a lot of the toil, cost and frustration of security from users and enable them to provide not only better security internally, but also enter new markets, gain customer trust and expand revenue opportunities, which is what the business actually cares about. As much as it may pain us in cybersecurity to admit, most organizations core competency isn’t in CVEs, vulnerability management, dependencies, security controls, compliance frameworks and all of the things we live and breath in security. Their core competencies instead are often in delivering some form of value to their customers and stakeholders and often security and compliance (arguably rightfully) is viewed as a tax, or a cost of doing business. Leaning into hardened images frees teams up from the monotony and frustration of dealing with massive security technical debt and exponentially growing vulnerability backlogs. This all has a cost with it, and as it turns out, it is quite substantial too! I previously published an article titled “CVE Cost Conundrums” where I broke down key findings from Chainguard’s “Cost of a CVE” report from 2025. The report alarmingly found that on average organizations that take a DIY CVE remediation approach spend $2.1 million annually, with some industries having even higher potential cost savings when they outsourced CVE remediation. While the cost figures may be new information for many, the reality that vulnerability management is difficult isn’t, and doing it at scale for many customers is even more difficult, something Chainguard themselves broke down in a blog titled “This Shit is Hard: Inside the Chainguard Factory”. Organizations that go at it alone, focusing on hardening images spend hundreds of thousands and even millions of dollars on doing so. It isn’t just money either, as there are opportunity costs associated with dedicating resources and individuals to these activities when they could have been better spent focusing on an organizations core competencies and driving revenue growth, customer attraction and providing value to stakeholders. These challenges exist for organizations looking to establish FedRAMP-compliant containers as well, especially as FedRAMP is aligning with broader frameworks such as NIST’s Secure Software Development Framework (SSDF) and ensuring their vulnerability management requirements account for containerized applications and workloads as well. Luckily, Chainguard does have some great resources for establishing and sustaining FedRAMP-compliance containers, including 5 key tactics they call out, such as:
While each of these may seem “simple” on the surface, they are not quite so easy in practice, which is why I recommend checking out Chainguard’s actionable guide that breaks these 5 tactics down at depth below. Resilient Cyber is free today. But if you enjoyed this post, you can tell Resilient Cyber that their writing is valuable by pledging a future subscription. You won't be charged unless they enable payments. |
Similar newsletters
There are other similar shared emails that you might be interested in: