Elevating CTEM with Agentic Exposure Management
- Chris Hughes from Resilient Cyber <resilientcyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
One dominant trend this year is that we’re in the year(s) (some say decade!) of Agents. We’ve seen excitement from startups, investors, and industry leaders around Agentic AI and its transformative potential, including in cybersecurity. This includes the area of AppSec and Vulnerability Management, and one of the most systemic challenges in the entire industry is remediation and exposure management. We’ve seen prior trends in cybersecurity, such as DevSecOps and the shift left, which aim to move security and tooling earlier in the SDLC to identify vulnerabilities.
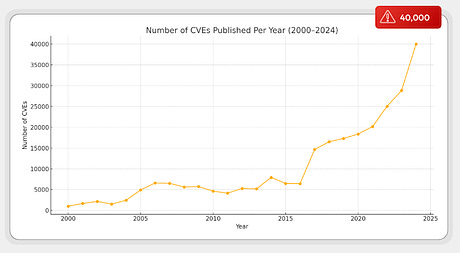
This is manifesting in massive vulnerability backlogs, often numbering in the hundreds of thousands to millions in large enterprise environments, and teams struggling with remediation and exposure management capacity. The number of new CVEs, both monthly and annually, significantly outpaces their ability to remediate them. We also know that we can’t “hire” our way out of this, as trends, such as the IANS 2025 Security Budget Benchmark Report, show cybersecurity budget growth slowing or even stagnating in some surveys. As shown below, this is impacting budgets, investments, staffing, and other critical areas, all of which are essential for effective remediation. That is why agentic AI is a promising capability with the potential to help address these longstanding challenges we can’t necessarily spend or hire our way out of and that have historically frustrated our development and engineering peers as well. We’re even seeing calls from industry leaders, such as the former four-star Chief of the NSA and Cyber Command, and the founder of the Pentagon’s Joint Artificial Intelligence Center (JAIC), who are calling for defenders to adopt AI for defensive cyber operations quickly. This comes on the heels of examples of attackers using Agentic AI to accelerate and amplify their own activities, such as Anthropic’s report of a AI-driven cyber espionage campaign. Few teams are pioneering this frontier, though, which is why I’m excited to take a look at one of them and their new approach. That team is Zafran, a leader in Continuous Threat and Exposure Management (CTEM), a topic I’ve covered in a prior blog titled “Vulnerability Management Evolves to CTEM”. In this follow-up piece, I’ll take a look at their new Agentic Exposure Management capability and how it addresses the enterprise vulnerability dilemma. Agentic Exposure ManagementTeams historically painfully stumble through exposure management activities manually. Investigating vulnerabilities, trying to correlate them to assets, understanding what is actively or likely to be exploitable, what mitigating controls are in place, what the business criticality is and much more. I’ve been advocating for some time the need for cybersecurity to pivot from its reputation as a laggard and late adopter of emerging technologies, to being an early adopter and innovator with this latest technological wave in AI. If we fail to reverse “cross the chasm”, we risk falling even further behind both our business and development peers, as well as attackers. That’s why I was really excited and impressed to see Zafran’s promising implementation of AI when it comes to exposure management. They set out to get teams out of the business of laborious data collection and focus on being able to take decisive actions, with deep relevant context on organizational exposure. While most collectively agree on the importance of maturing beyond traditional vulnerability management to exposure management, the amount of data and context required to enable effective actions is overwhelming.
Zafran is striving to tackle this with their AI-Native Exposure Graph, which helps consolidate assets and findings, with robust integrations and partnerships with leading security vendors and tools commonly in cybersecurity tech stacks, along with risk context, such as Internet reachability and runtime presence among others. It also adds context tied to organizational defenses, such as network, endpoint and cloud environments and what security tools, implementations and configurations organizations have in place that play a role in their exposure. This AI-native approach, coupled with rich context of organizational tools, systems and environments enables real actionable opportunities to drive down exposures and risks. While there’s been prior waves of promised automation, they often required a constant detailed curation of playbooks and processes. What makes Agentic AI unique is the ability for it to constantly learn, evolve and iterate on its own, coupled with human oversight to avoid unintended outcomes. Zafran isn’t just talking about the potential of Agentic Exposure Management either, but showing it. They lay out several real-world examples, such as zero day exposure assessment and identifying the top exploited vulnerabilities in your environments. Agents are able to be unleashed to carry out historically manual and cumbersome activities, such as validating what’s exploitable, identifying relevant asset owners, determining the impact of a patch and even providing robust remediation plans and reporting. It’s easy to see how this promising use case of AI can not only streamline traditional aspects of exposure management, but as organizations adoption of AI and Agents evolves, potentially move towards fully agentic and automated remediation activities, alleviating one of the most problematic and pervasive aspects of exposure management - actually fixing what gets found. The potential to do so while avoiding bogging down developers or the business, which has often led to frustrations and disengagement with security can also address deep cultural rifts between security, development and engineering while not impeding development velocity in an era where it’s faster than ever.
Zafran demonstrates how an agent can work collaboratively with a user to definitively assess if a finding is a false positive and produce a report accordingly. The amount of time this can save organizations is far from trivial. It has been covered by industry analysts, such as Katie Norton of IDC, whom I previously interviewed on AppSec trends. Zafran also advocates for what they call a “Closed-Loop System”, similar to the iterative development lifecycle in software, that involves the four steps below: These components are key to effective exposure management and are aligned with leveraging agents as a force multiplier. Agents can proactively identify exploitable vulnerabilities in runtime environments, underpinned by scalable data and queries, which enable them to interact with potentially affected assets in real-time, often through the use of tools. As we progress through the maturity curve and become more comfortable with agentic AI, we’re likely to see this process initiated semi-autonomously, with human oversight, and potentially, in time, fully autonomous, eliminating the need for human users to intervene between exposure identification and automated remediation. This maturity curve of autonomous adoption is also something I discussed earlier this year at RSAC, as part of the OWASP GenAI Project’s AI Security Summit. One aspect of their approach and perspective that really resonates with me is the tremendous potential this holds for existing environments. While teams should still “shift left” and inject security into the SDLC, including leveraging agents and AI to enhance SAST, SCA, etc., there is no denying the need for runtime agent-based remediation. I’ve written extensively about topics such as Application Detection & Response (ADR), including articles like “How ADR Addresses Gaps in the Detection and Response Landscape.” We can all openly acknowledge that no organization can prevent all vulnerabilities from entering runtime production environments. The fact is that large enterprises have massive vulnerability backlogs, much of which is tied to assets, software, and systems already running in production and potentially exposed to malicious actors. We already know, from evidence provided by leaders such as Anthropic and others, that hackers are and will continue to increase their use of agentic AI to maximize their impact and damage. I’m a strong believer that defenders should also look to do the same to bolster their defensive cybersecurity postures. Zafran’s Agentic Exposure Management capability is a promising step towards leveraging AI for security and alleviating the Sisyphean task of vulnerability remediation that nearly all organizations struggle with.  Looking to transition from legacy Vulnerability Management to Continuous Threat Exposure Management (CTEM), while leveraging the benefits of agentic remediation? Check out Zafran’s “Practical Guide: Evolving from VM to CTEM” “We should not cede the cyber advantage derived from AI to attackers and criminals.” Resilient Cyber is free today. But if you enjoyed this post, you can tell Resilient Cyber that their writing is valuable by pledging a future subscription. You won't be charged unless they enable payments. |
Similar newsletters
There are other similar shared emails that you might be interested in: