Resilient Cyber Newsletter #55
- Chris Hughes from Resilient Cyber <resilientcyber+resilient-cyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
Resilient Cyber Newsletter #5510 Immutable Laws of Cyber, NATSEC 100, AI Regulation Contrasts, LLMs and Secure Coding, Application Attack Matrix & fwd:cloudsec SummariesWelcomeWelcome to issue #55 of the Resilient Cyber Newsletter. I hope everyone is enjoying summer, as I know it is going well on my end. As I mentioned, I recently visited Northern Virginia to watch my son compete in the Virginia Little League State Championship this past weekend. We made it to the quarter finals but lost to a Northern Virginia team. Apparently, my NOVA friends are a little league powerhouse, boasting several teams making it to the finals! But, enough about me, this week we have a lot of awesome cyber resources to dive into, including a look at how immutable laws of cyber still stand strong 25 years later, AI regulatory contrasts between the U.S. and EU, using LLMs to produce secure code (or not) and the introduction of an Application Attack Matrix among much more. So, here we go! Interested in sponsoring an issue of Resilient Cyber? This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives Reach out below!
Cyber Leadership & Market DynamicsThe Cybersecurity Job Market is Broken - And Everyone Knows ItIn a damning piece from Tracey Webb, he calls out the cybersecurity job market, arguing that CISOs and security leaders have outsourced critical hiring functions in Cyber to HR, AI and keyword searches. The post must have resonated, as it garnered several hundred interactions and nearly 100 shares on LinkedIn. The piece raises points that remind me of a piece I shared earlier this year from Chase Cunningham, who said rampant layoffs weren’t due to AI, but companies just looking to maximize profit and cut expenses (labor). There’s truth to this piece, but I would also say that struggling folks often miss critical activities such as building a deep network, building a personal brand/reputation, staying relevant in the domain knowledge of emerging technologies, and more. It’s a two-way street. While hiring is getting more difficult due to ridiculous position descriptions, requirements, automation, and outsourcing to HR, we also need to do everything we can to ensure we’re in a position to be highly in demand and marketable from a labor perspective. Black Hat Startup Spotlight Competition FinalistsOne of the largest cybersecurity conferences is around the corner, in Black Hat. Much like RSA, this event has an angle that looks to highlight the most innovative and disruptive startups, and their recent “Startup Spotlight Competition” finalists were recently announced. They include:
As seen above, the judging panel also made honorable mention of 5 other firms. Watching the finalists' presentations and seeing who walks away from the event at the top will be exciting! Reflecting on “10 Immutable Laws of Security” 25 Years LaterMy friend Ross Haleliuk recently wrote a piece on Microsoft’s Security Response Center’s 10 Immutable Laws of Security, which are now more than two decades old and are framed as fundamental truths related to cybersecurity. As MSFT pointed out way back, the origin of security issues is much more closely related to the nature of systems, people, and trust than to any specific code or bugs, almost like universal laws of nature. The laws are inevitably spot on, and what’s ironic is how painfully true they are, but we still counterintuitively violate their principles. See below for some examples:
Ross does a great job covering the 10 Laws and how they are as true as ever, while also weaving in relevant context about how the landscape and technology have changed in the past 2+ decades. The Cybercriminal Group Wreaking Havoc on Corporate AmericaThis piece from Axious highlighted the ongoing activity of “Scattered Spider,” a hacking group that has been targeting retailers, grocery chains, insurance providers, and airlines across the U.S. using techniques such as help desk impersonation and SIM Swapping. One thing that makes the group unique is that it isn’t a mature, organized hacking group but a loose coalition of young men and teenagers who came out of the gaming community and are using ransomware to impact their victims. Despite their age and loose nature, they have an internal organizational structure, tiered positions of maturity, and run like an actual business. While they have made recent headlines, they first gained fame by hacking MGM Resorts and Caesars Entertainment in 2023 and are largely using the same techniques today with much success. This highlights the bleak nature of most modern corporate cybersecurity. Industry leader Jen Easterly took to LinkedIn, calling the group “Scumbag Spider” instead, and stating they aren’t ninjas and are using attack techniques that could be mitigated by a Secure-by-Design/Demand approach from industry. She stated:
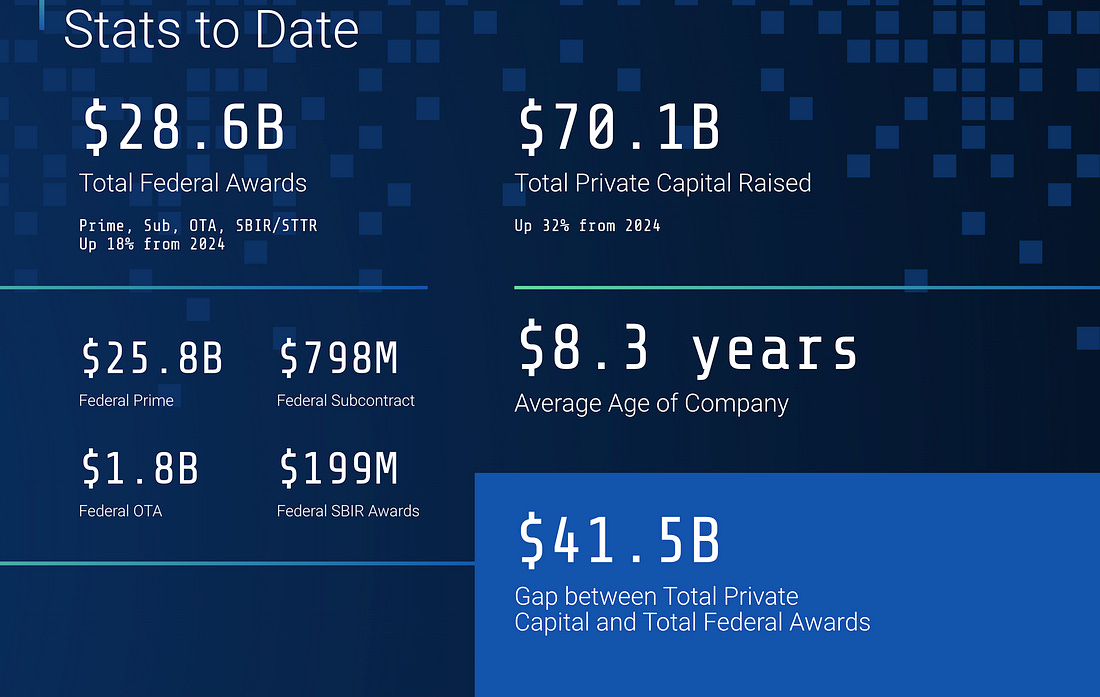
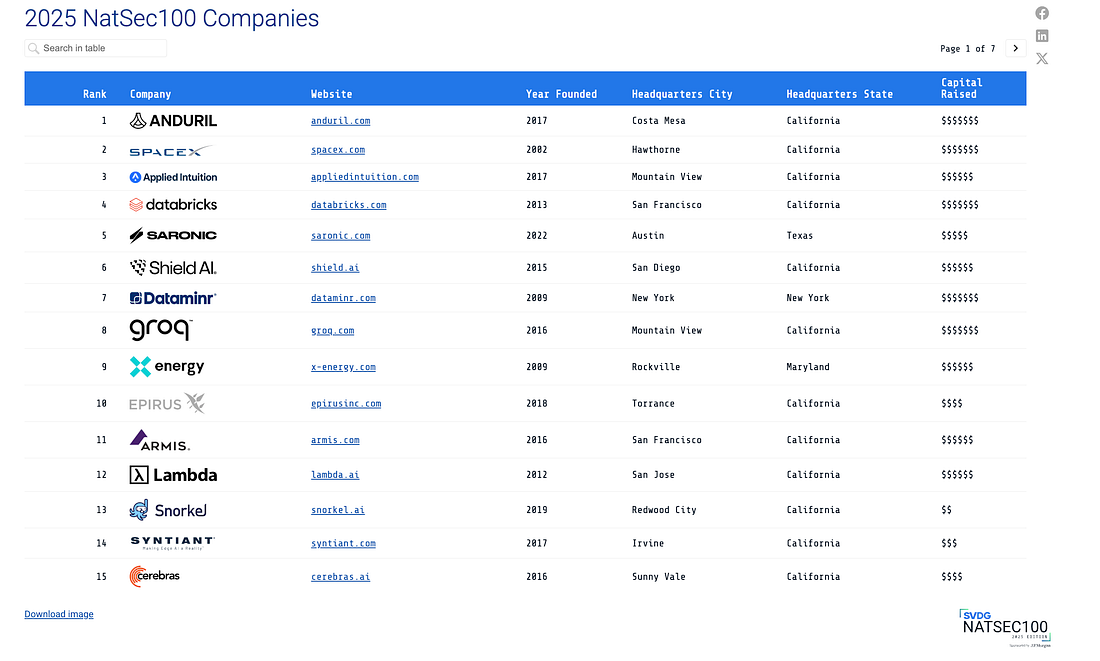
Silicon Valley Defense Group (SVDG) NATSEC 100 - 2025 EditionI spend a fair amount of my time focused on the public sector, including DoD, due to my role as the Co-Founder and CEO of a Public Sector-focused digital services firm, Aquia. That’s why the SVDG NATSEC 100 caught my attention this week. Produced in partnership with JP Morgan, it provides insights into the top 100 venture-backed, dual-use, and defense technology companies focused on national security. The report cites in 2024 they saw a ~2.3x increase in prior year spend by the DoD on NatSec 100 companies, which isn’t too surprising for those paying attention, as the current administration had a strong backing from silicon valley and venture capital as well as a mandate to try and disrupt the status quo in terms of primes and vendors. The report also points out that this still accounts for <1% of the total DoD budget, emphasizing just how dominant the traditional DoD primes are. Another interesting anecdote is that they offer their analysis and dataset with and without SpaceX, due to its outsized funding, as well as its outsized Government contracts compared to the rest of the NatSec 100, which again for those following politics, could be an interesting thing to keep an eye on given the tension between President Trump and Elon. Below is a snapshot of some of their key stats/findings: Also, the top 15 companies ranked: The report is worth reading if you’re interested in and passionate about the DoD market from a technology and capital perspective. AIAI Patchwork Quilt of Regulation ForthcomingAs part of the recent “Big Beautiful Bill,” a 10-year moratorium (e.g., a ban) on state-level AI compliance and regulation was proposed, but it was recently struck down and removed from the bill's version that passed. This is a dynamic topic that has valid arguments in both directions. On one hand, AI is too immature and evolving to be regulated effectively. Efforts to do so could hinder innovation and lead to economic and national security consequences for the U.S. (and others). On the other hand, it could be argued that we need a comprehensive, cohesive compliance regime to avoid a patchwork quilt of state-level regulations that will be costly and cumbersome for businesses to navigate and impose challenges and impacts on consumers. Citizens of different states/nations could be constrained regarding what innovative AI services, products, models, etc., they can access. We’re headed for that patchwork quilt, as the 10-year state-level ban was removed from the passed bill. Many states have already ushered in one or more AI regulatory requirements that businesses must now navigate. This topic, as discussed in major news outlets such as AP and many others, involves many dynamics and angles, from differences between the two parties to big techs pushing for the moratorium, to states looking to assert their rights to regulate. In the absence of a coherent Federal-level AI regulatory regime, states are expected to step in, much like they’ve done with privacy here in the US. The AI Regulatory Moratorium Fails: What Comes Next?In the wake of the 10-year regulatory moratorium failing, some have penned strong opinions on what will happen next. This includes Adam Thierer, who details some of the policy and even national security and economic implications in this piece. Adam makes three primary arguments:
While some may find Adam’s arguments flawed, he raises some good points. In security and compliance, we often use the phrase “high water mark” to meet the most rigorous compliance requirements upfront. Many tech and AI organizations will inevitably be forced to meet the most stringent U.S. (and global) AI regulatory requirements, such as those from NY and CA, regardless of what the other states say or do, due to the reality that it is too costly and impractical to have countless different products and services for each state. Adam argued that the irony is that much of the animosity around the moratorium was directed at “Big Tech.” Still, those big firms are the ones who will be able to navigate the costly and confusing patchwork AI regulatory model where they are headed, with smaller firms struggling to manage the cost and complexity of compliance. I have seen this play out in areas such as FedRAMP and the DoD SRG related to Cloud and ATO’s in the public sector, as larger firms can afford the time and cost to meet the compliance requirements, and afford to enter these markets, essentially locking out smaller firms with less resources, even if they have innovative products and services the industry could benefit from. To his last point about impacting a pro-innovation and pro-investment policy approach to compete with China for AI leadership, one of the best ways to mitigate what is happening would be for the Federal government to take the lead with a coherent, cohesive approach to AI regulation, mitigating the states’ need to step in. That said, of course, some states, such as CA/NY, can and will impose their regulatory requirements, but this would at least provide a uniform Federal pathway for industry and also allow companies to avoid some states if needed while still driving the nation forward from a competitive and innovative perspective. However, watching how we have failed to do something similar around Privacy will leave those of us watching this AI regulatory battle with a sense of déjà vu. Europe’s Biggest Companies Call for a Two-Year Pause on EU’s Landmark AI ActNot to be left out of the conversation, our friends in the EU saw action on AI regulation recently, too. A coalition of Europe’s largest companies asked for a two-year freeze on the implementation of the EU’s AI Act, citing concerns it could impede the EU’s ability to keep pace with China and the U.S. It will be very interesting to see how this plays out, given the EU by its own admission in some ways has set out to be a “regulatory superpower” despite many concerns from national and industry leaders alike who state the heavy handed compliance approach of t he EU is impacting the EU’s ability to compete and also its economic prosperity and national security. And, right on cue, as expected, EU leaders stated “No pause for the EU AI Act Implementation timelines”. The EU government and bureaucracy seem to be committed to this path, regardless of the impact on economics or national security.
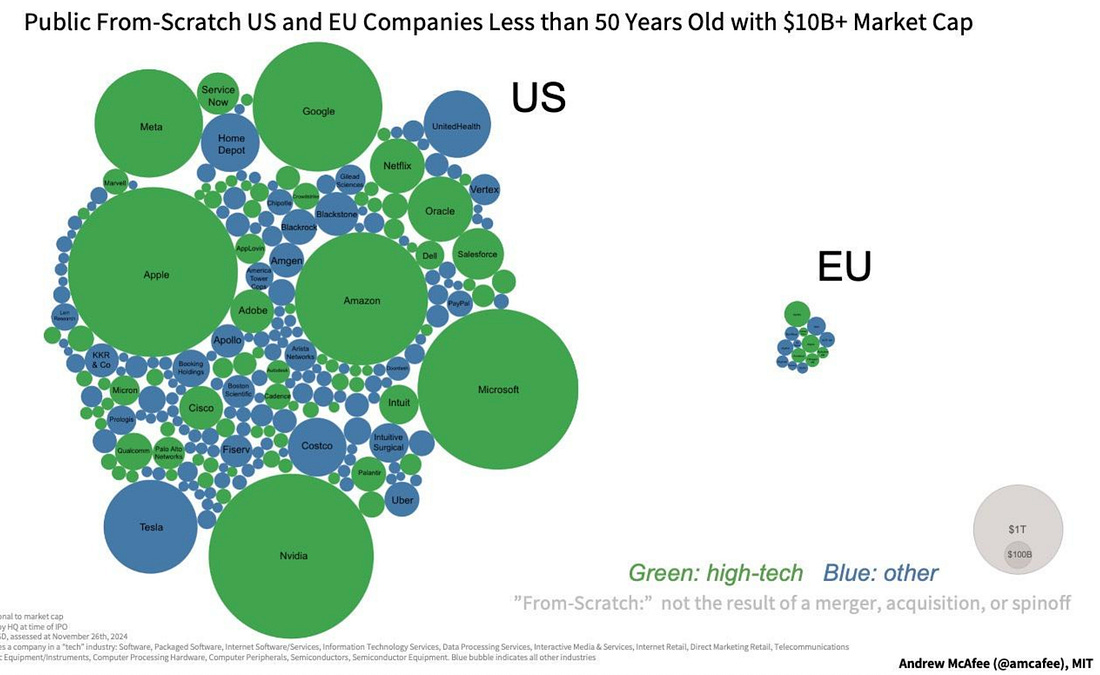
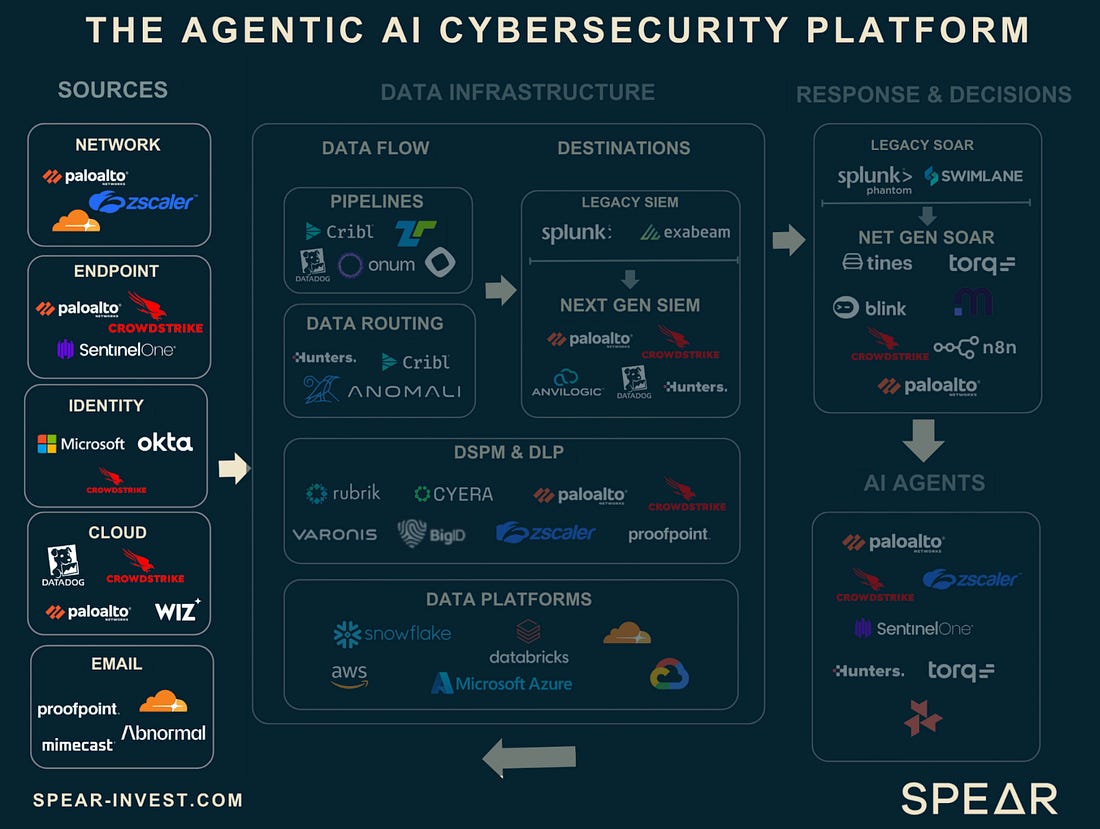
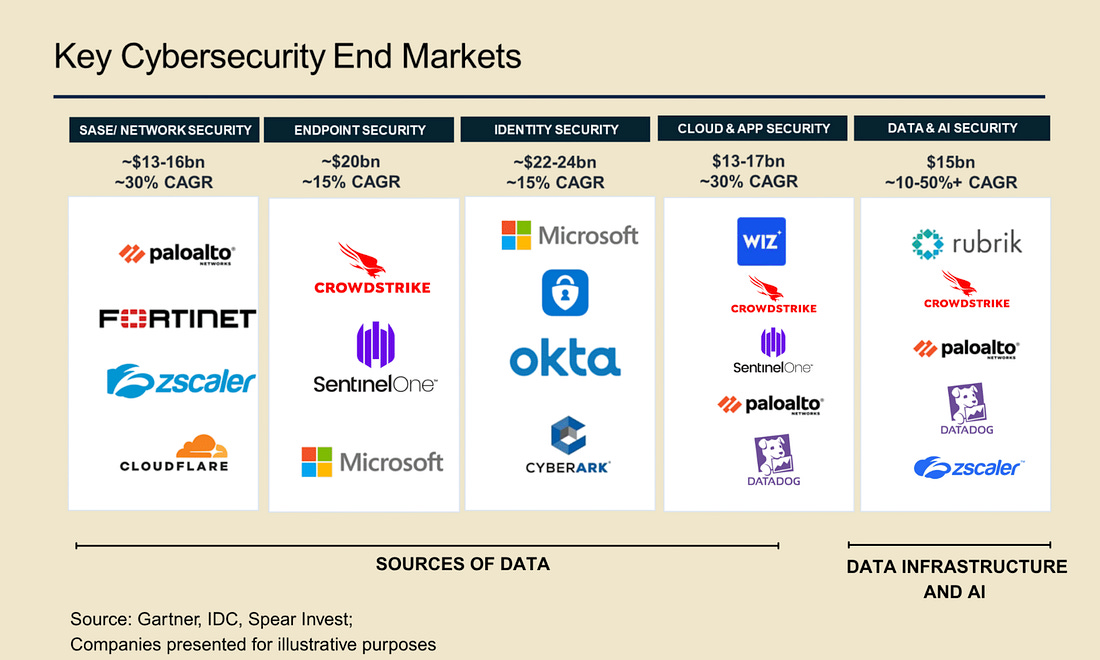
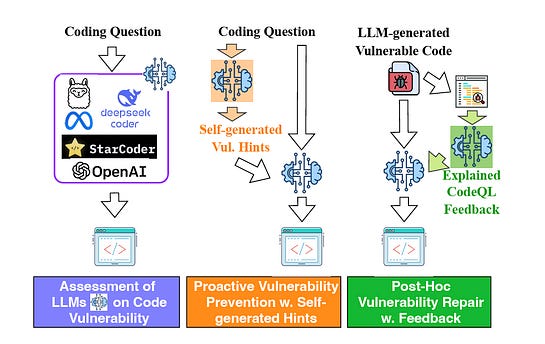
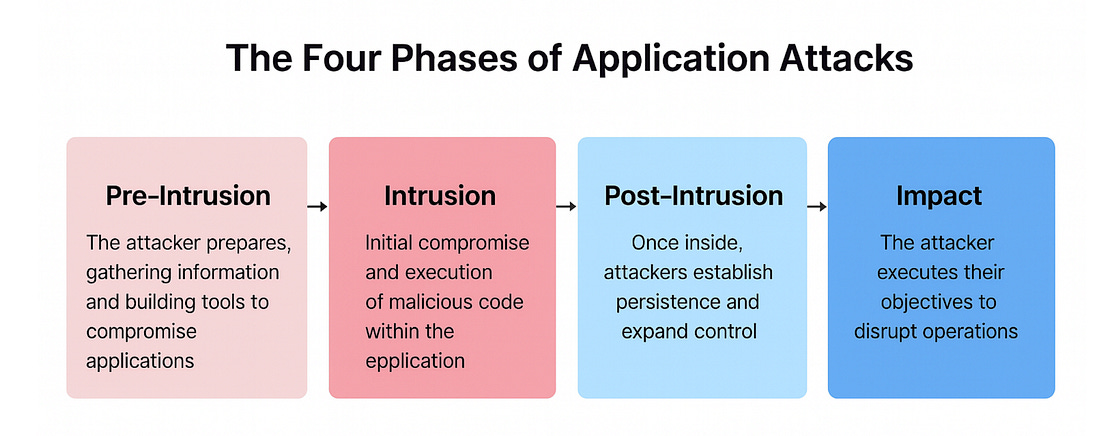
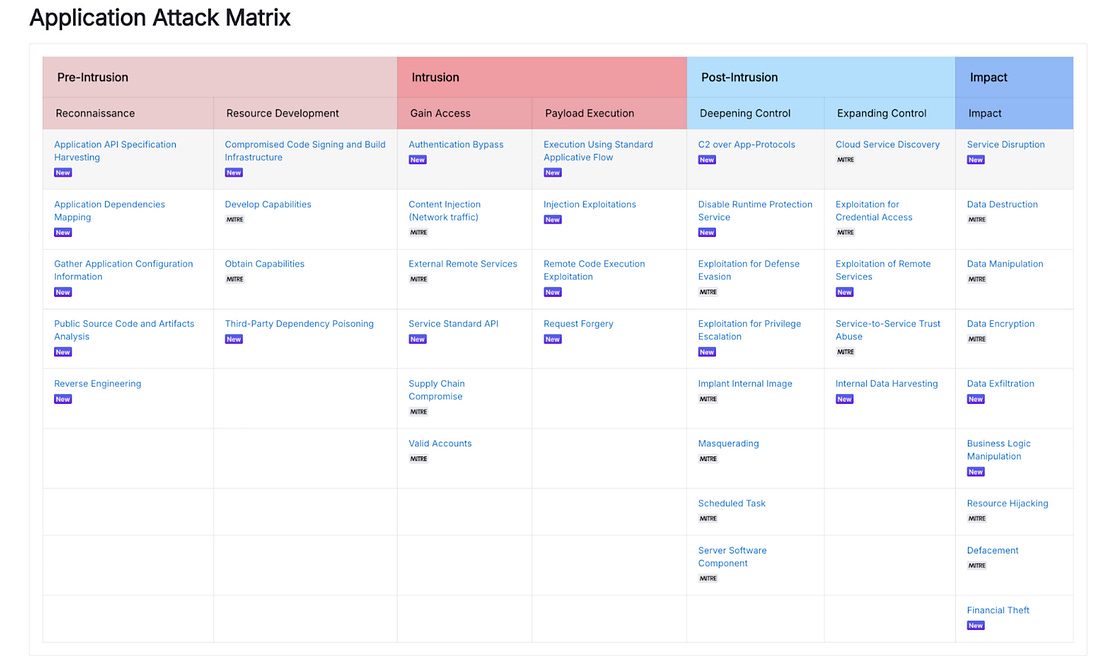
I always enjoy sharing the below diagram as a stark reminder of just how different the US and EU ecosystem for growth and high-tech are: The Rise of the Agentic SOCThe industry continues to be enamored by AI's potential to transform cybersecurity, including in key areas such as SecOps with the SOC. This piece from Spear Investments explores the topic, looking at technical and market factors driving this focus. The piece emphasizes what is foundational to Agentic SOC operations, which are the data sources and data infrastructure layer. As seen in the image above, this is no small feat and often involves a complex combination of systems, products, and environments to bring things together. As the authors point out, the modern SOC isn’t a static dashboard, but instead a system built on robust real-time data sources providing actionable insights, and can come from sources such as the network, endpoints, identity, and cloud environments. The industry leaders, such as Crowdstrike and ZScaler, have a significant advantage when it comes to data, given each protects billions of digital assets and/or processes billions and even trillions of transactions, providing them a massive data set to drive higher fidelity insights and even further train models tied to products. This data “moat” is a point the CEO of Horizon3AI, whom I respect, has often cited as key. From an investor’s perspective, each of these areas of the cyber market has and continues to see double-digit growth annually, as depicted below: The piece goes on to break down each of these key cybersecurity end markets, leading vendors, disruptors, and the complexity involved within each category defined above. It then discusses how they all provide insights key to powering the future agentic SOC. Can LLMs Develop Secure Code?As it turns out, it depends. A recent paper found that smaller specialized models, coupled with security-centric prompting and guidance, can develop more secure code. While the results seem promising, I inevitably think about reality versus academia and research. This means the attack surface is poised to grow exponentially as Developers use vanilla prompts for code generation with little to no context added for security and hardened code, inherently trusting whatever the models output for the sake of moving fast, as developers are incentivized to do. AppSec, Vulnerability Management & Software Supply ChainThis Sh*t Is Hard: Vulnerability Scanner IntegrationContinuing their series about activities that are difficult behind the scenes that organizations grapple with, Chainguard recently released a piece discussing vulnerability scanner integration. They outline the challenges of dealing with multiple vulnerability databases, which often have duplicative information, conflicting data, and disparate IDs, making vulnerability scanning and management difficult. Chainguard also describes its internal processes and the tools it uses to identify and communicate vulnerabilities to customers. This activity leads to remediating vulnerabilities, communicating changes to customers in advisories, and providing context-rich information from which scanners can pull. Chainguard summarizes the difficulties, including the reality that there are tens of thousands of vulnerabilities every year, many captured in NVD and other vulnerability databases, many different vulnerability scanning tools, the need for context, and much more. This blog is a great peek behind the curtain of vulnerability management as a software vendor. The Application Attack Matrix 🧨Several of the industry-leading reports, from M-Trends to DBIR, show that application exploits are on the rise as one of the most dominant attack vectors. fwd:cloudsec SummariesOne of the leading cloud security conferences of the year recently took place, bringing together industry-leading experts with deep experience in various CSPs, multi-cloud, identity, AppSec, and more. The playlist is live, but it can be difficult to keep up with, with 43 talks covering various topics and domains. Luckily, this repository puts it all together neatly and well organized, allowing you to focus on the most interesting topics. It breaks the 43 talks down into the following categories:
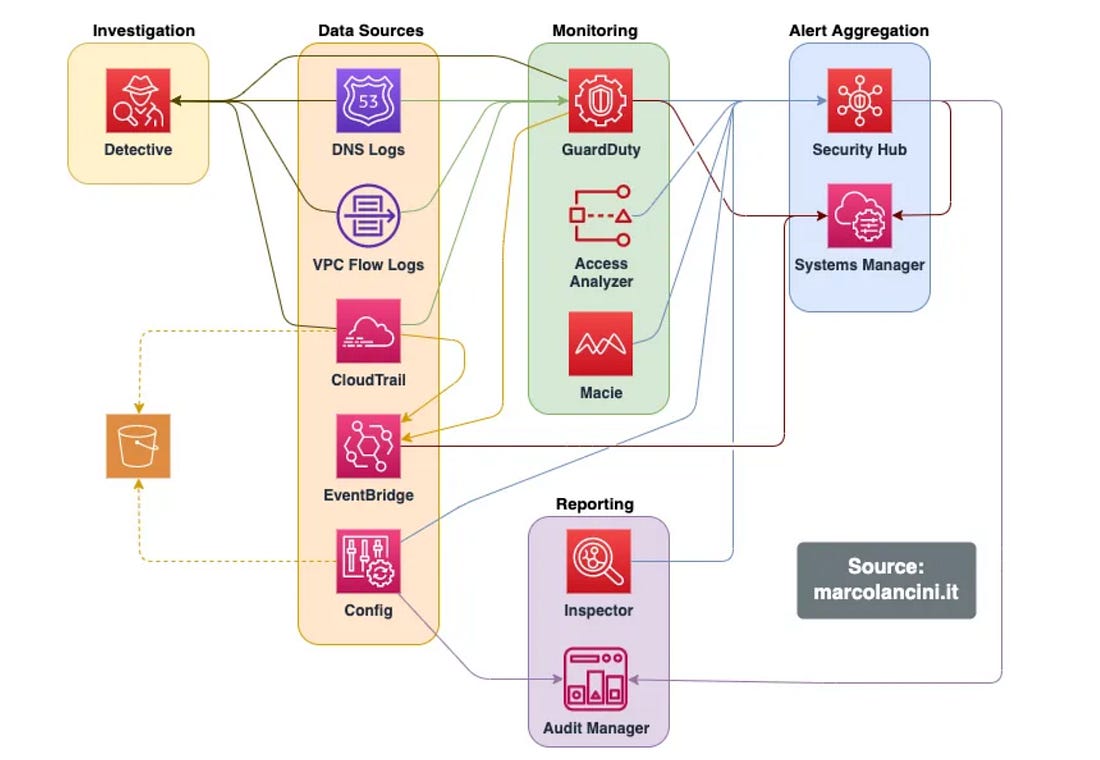
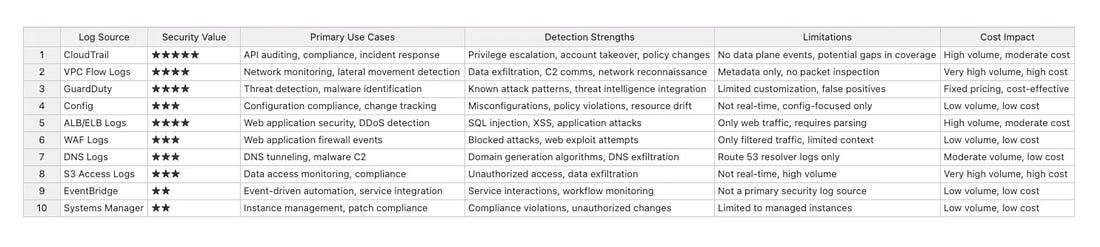
From AWS Detection Deficit to Detection MaturityBuilding robust and effective detection capabilities in leading CSPs such as AWS can be a complex endeavor, even for the most capable teams. This incredible blog detailing how one team identified their AWS detection deficits and matured them while diving deep into AWS log sources and telemetry is helpful for any security practitioner securing workloads in AWS. The below image helps highlight the AWS services involved, both from a data source, monitoring, and aggregating perspective. The author lays out an AWS Log Source Security Summary: They discuss how they built out detections and enriched log sources with additional information such as network context and threat intelligence, where possible, to provide deeper insights. Their journey captures key lessons as well:
Non-Human Identity (NHI) Discussion NHI’s continue to be a hot topic, and something I have written and spoken a lot about, including with my friends at Astrix Security. That said, I found this discussion with investor Pramod Gosavi and the founder of Clutch Security to be a good one, covering a wide range of topics related to NHI’s, such as:
Resilient Cyber is free today. But if you enjoyed this post, you can tell Resilient Cyber that their writing is valuable by pledging a future subscription. You won't be charged unless they enable payments. |
Similar newsletters
There are other similar shared emails that you might be interested in: