Resilient Cyber Newsletter #78
- Chris Hughes from Resilient Cyber <resilientcyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
Resilient Cyber Newsletter #78Inside the Trillion Dollar AI Buildout, Shaky Foundations of Vibe Coding, MCP from the Trenches, Agentic Browser Threat Modeling, 2025 State of LLMs & the Growth of CVEsWelcome!Welcome to issue #78 of the Resilient Cyber Newsletter. This is the first official newsletter release of 2026. I hope everyone had a great break for Christmas and New Years with friends and family and is as recharged as I am to hit 2026! I’ve got a lot of great resources and discussions to share this week, including a comprehensive breakdown of the trillion dollar AI buildout, growing concerns about the sustainability of vibe coding, a deep dive into the state of MCP in the enterprise and a look at threat modeling the rise of Agentic browsers. All this and more this week, so here’s to an amazing 2026, where AI will inevitably continue to shape not just cybersecurity but the entire software ecosystem. Interested in sponsoring an issue of Resilient Cyber? This includes reaching over 40,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives Reach out below! Cyber Leadership & Market DynamicsAI-Orchestrated Cyber Espionage and the Future of Cyber DefenseAnthropic’s report of AI-orchestrated cyber espionage made headlines recently, and that includes catching the attention of those in the U.S. Government, at agencies such as CISA. In this discussion with Nick Andersen the Executive Assistant Director for the Cyber division within CISA, Nick discusses the role of AI and its impact on both cyber offense and defense and how CISA and the Federal government is thinking about the future of cyber defense.  Jevons Paradox for Knowledge WorkWe've heard a lot this year about the role of AI and its impact on knowledge work, the labor market and employment. This is an anteresting piece from Aaron Levie, CEO of Box, where he states when discussing AI and Agents many overemphasize the “R” of ROI and under-examine the “I”. Satya Nadella describes how lessons from Microsoft’s history apply to today’s boomAs I mentioned, I’ve been using time during the holiday break to catch up on some great conversations I had saved and queued up. Among them was this wide ranging interview with Microsoft’s CEO Satya Nadella. Satya goes through a lot of great topics, from Microsoft’s history to the current AI boom and everything in between. What I was fascinated by was Satya’s range, as he navigated from complex technical topics to business and financially focused aspects of the conversation, but I suppose that’s why he leads one of the most dominant tech giants in the world!  AIInside the Trillion Dollar AI BuildoutI used Christmas/New Years break to catch up on great discussions I had saved. Among them was Dylan Patel’s interview about all things AI. While the title does focus on the massive capital intensive AI buildout, Dylan touches on way more than just infrastructure buildouts, covering topics ranging from coding, talent wars, competition among the model providers and way more. Dylan is easily one of the most knowledgeable and informative folks to follow on all things AI.  Prompt Injection - Vulnerability or Not?ne topic that has led to a lot of debate in recent months is whether or not Prompt Injection is a vulnerability in LLMs or not. Groups such as OpenAI have openly said it is likely never to be solved and we continue to see countless examples of security researchers and product vendors trying to dunk on AI products by doing direct and indirect prompt injection attacks. Vibe Coding Leads to Shaky FoundationsThat’s one of the takeaways from Cursor’s CEO’s comments recently to Fortune. In 2025 we saw the rapid rise of “Vibe Coding” as the development community, much to the dismay of cybersecurity, leaned into AI coding tools and just implicitly trusting outputs. That said, the term also became a catch-all, and mistakenly used to refer to any AI-driven development, even when being wielded by highly proficient developers with deep domain expertise.  Planning a Successful AI Rollout in CybersecurityThere’s been a lot of stories of problematic AI rollouts across enterprise environments. Cybersecurity isn’t immune from botched rollouts either, which is why I found this piece from Alain Mayer and David Seidman to be a good one. They lay out key concepts and a structured approach to rolling out AI in Cyber, including:
This is a practical and well grounded piece that can be used to help establish a sound approach to rolling AI out, not just in Cyber, but beyond as well. The key theme in their piece is you have to know what you’re hoping to accomplish and how well you’re doing it currently before deploying AI or being able to understand its ROI. Unfortunately, many are doing the opposite and rushing into adoption with no clear picture of where they are now, let alone where they hope to go. The Normalization of Deviance in AI
A tale as old as time when it comes to cybersecurity, and it is one we're watching unfold both in the sense of frontier model and platform providers, as well as in the macro sense across enterprise environments where the competitive pressures to outpace and out innovate competitors drives the normalization of insecure behaviors and practices. This is a great piece discussing how temporary shortcuts become the new baseline, as deviance from secure practices and methodologies get normalized. The Biggest Impediment to AI Outcomes is Organizational ReadinessThat was the key point made recently by Mike Krieger, CPO of Anthropic. He pointed out how AI is quite capable now, in terms of knowledge, activities, tool use and so on, but organizations have a long way to go in terms of maturity to move towards widespread AI implementation and business outcomes. To successfully use Claude and others leading AI tools for business outcomes will require clear requirements and goals, along with providing adequate information to the LLMs and Agents.
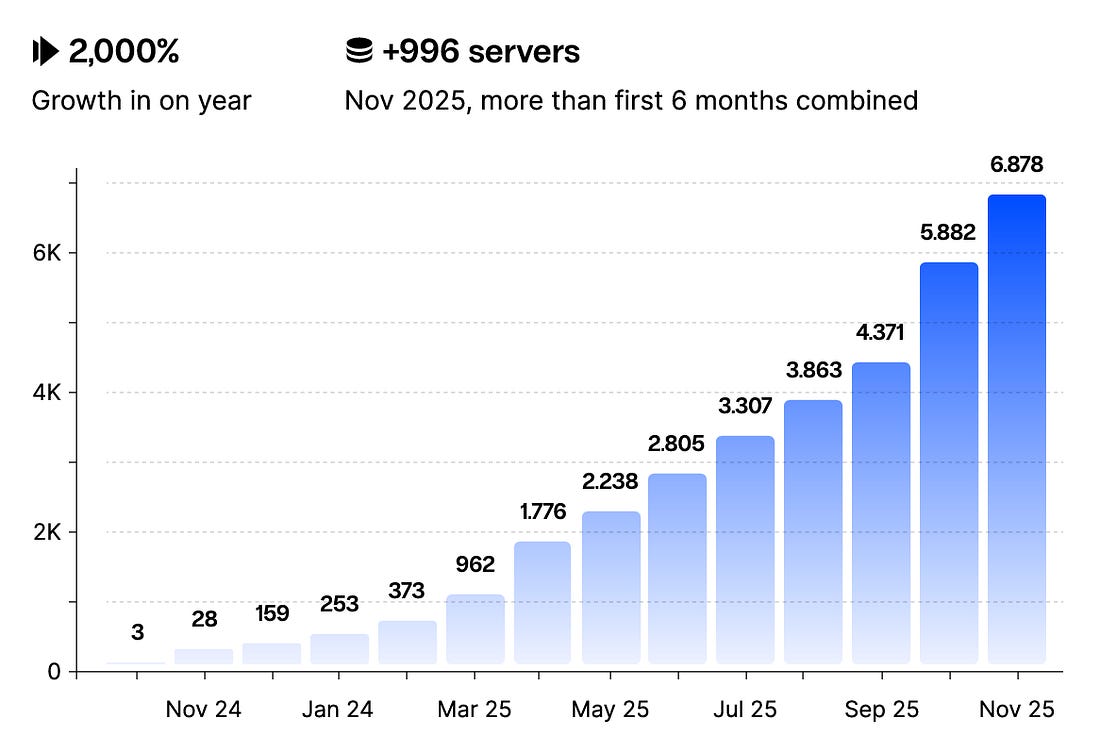
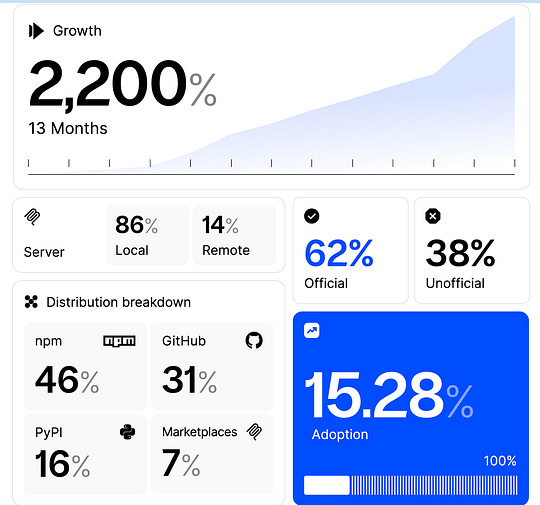
It also requires giving AI sufficient access, an area many are rightfully concerned with as we continue to see incidents impacting organizations, as well as the leading LLMs and Agentic platforms. See below for key items Mike emphasizes: This means organizations need to have clarity on the tasks they want AI to perform, give AI appropriate permissions (and be comfortable with doing so) and have stable processes that can be programmatically executed repeatedly at-scale. As many who’ve worked in complex organizations, while this may sound simple, it is anything but. Given how the MIT report on the success of AI efforts and outcomes rocked the industry in 2025, it will be key to see if we can move beyond the headlines to actually drive measurable ROI with AI efforts. MCP: A View from the TrenchesThe Model Context Protocol (MCP) from Anthropic took the industry by storm this year. Suddenly it was something everyone was talking about and every vendor seemed to create an MCP server and integrate MCP into their offerings. But, what does it look like under the hood in terms of adoption and risks?
This report is full of great insights and is well worth a read if you’re looking to understand the growth of MCP as well as the associated risks. Agentic Browser Threat ModelingAnother key trend among the broader Agentic AI wave in 2025 was that of Agentic Browsers. ChatGPT's Atlas, Perplexity's Comet, and the latest example being Claude in Chrome. The opportunity sounds promising, especially given how much time users spend in the browser and the ability to streamline, automate and amplify activities across the web and countless web-based applications. This piece from the team at Zenity highlights key concerns from indirect prompt injection, destructive actions, sensitive data disclosure, lateral movement and user impersonation. Most of a users time is often spent in the browser, including managing cloud infrastructure, monitoring, accessing systems with sensitive organizational data and in the age of AI, accessing sites and data which may lead to incidents (e.g. indirect prompt injection) in various forms, all while inheriting the permissions and persona of the users in the browser. Hardening OpenAl’s Atlas: The Relentless Challenge of Securing an Untrusted Browser AgentSpeaking of hardening and securely using Agentic Browsers, Zenity who published the prior excellent piece on Claude’s Chrome integration followed up it with another piece discussing OpenAI’s Atlas and how much of the hardening and secure usage of their Agentic Browser is being left to the user, including:
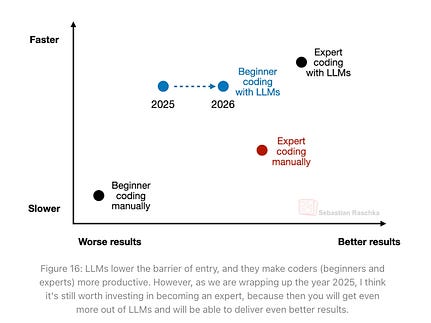
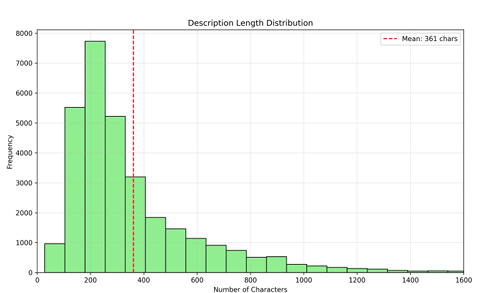
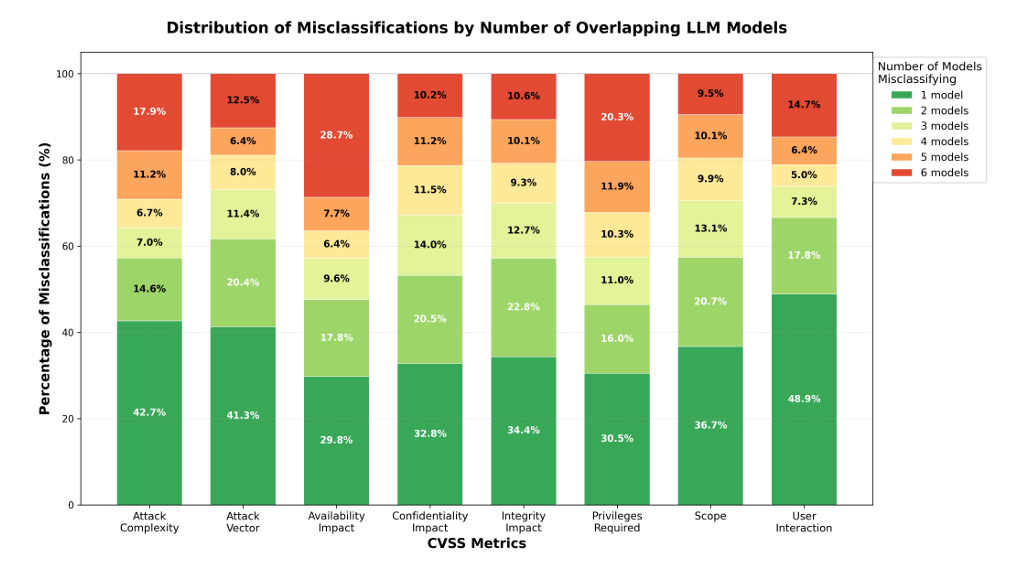
You don’t need to think to hard to realize that most users simply won’t take these precautions and lack the fundamental security awareness or experience to even think of these things during their daily usage. If and when Agentic Browsing becomes widespread, so will the risks of not doing the exact activities laid out above by OpenAI. The State of LLMs 2025: Progress, Problems and PredictionsTo say AI has and continues to advance quickly would be an understatement. That said it can be hard to keep up with the pace, even for leaders such as Andrej Karpathy, who recently shared his struggles with keeping up with the pace of changes AI is having on software development. This piece from Sebastian Raschka, PhD is an incredibly comprehensive breakdown on the State of LLMs in 2025, including the progress made, problems that remain and predictions moving forward. AppSecCan LLMs Quantify Vulnerabilities?We continue to see the industry look to apply AI, LLMs and Agents to countless use cases across many cybersecurity categories. One such a problematic area is that of assigning scores to vulnerabilities, specifically CVEs. They have helpful diagrams in the study showing the role that description length and other factors play too. Trust Wallet Compromised, Stealing $7M on Christmas EveThe team out of Koi continues to rapidly provide insights on software supply chain threats and malicious packages and extensions. The latest example comes via a crypto wallet named Trust Wallet, owned by Binance with over 1 million Chrome users. There was a malicious update pushed on Christmas Even, similar to the malicious Cyberhaven Chrome extension in 2024 on Christmas Eve. In this case, it resulted in roughly $7 million being drained from user wallets in under 48 hours. While it hasn’t been confirmed the threat actor is the Grinch, it sure as hell feels like it. Antiquity is a Superpower: Why legacy vendors are still winning in VulnMgt (for now)We continue to see the Vulnerability Management space evolve into a new category now being called Continuous Threat and Exposure Management (CTEM). It’s once I’ve written about before, in pieces such as “X”. In this piece, Mehul argues that antiquity is a super power and despite many looking to disrupt VulnMgt over the years, the legacy giants such as Tenable, Qualys and Rapid7 still reign supreme. To prove his point he uses the announcement of Kenna being End of Life. Mehul makes the argument that while innovative startups can try and tackle aspects of VulnMgt such as prioritization and remediation, but MVPs don’t cut it in this category and you must dominant in the aspects of vulnerability signatures and sensors/scanners to detect vulnerabilities. He states that Cisco looked at Kenna and saw a profitable acquisition target without realizing it lacked native capabilities to cover the aspects I mentioned above and were forced to try and build it, pay the incumbents for their signatures and sensors, or just shut things down. The reason he argues antiquity is a superpower is that these entrenched incumbent firms have decades of vulnerability signatures and sensor data and it is hard to replicate. Unlike the new startups, these entrenched incumbents cover all the corner cases, EoL software, antiquated products and more for their large longstanding enterprise customers. This is a feat not easily replaceable by the new cloud-native types who don’t have decades of product development backing their product for every obscure product and application you can imagine in terms of coverage. Mehul calls this the “long tail of signatures” and argues:
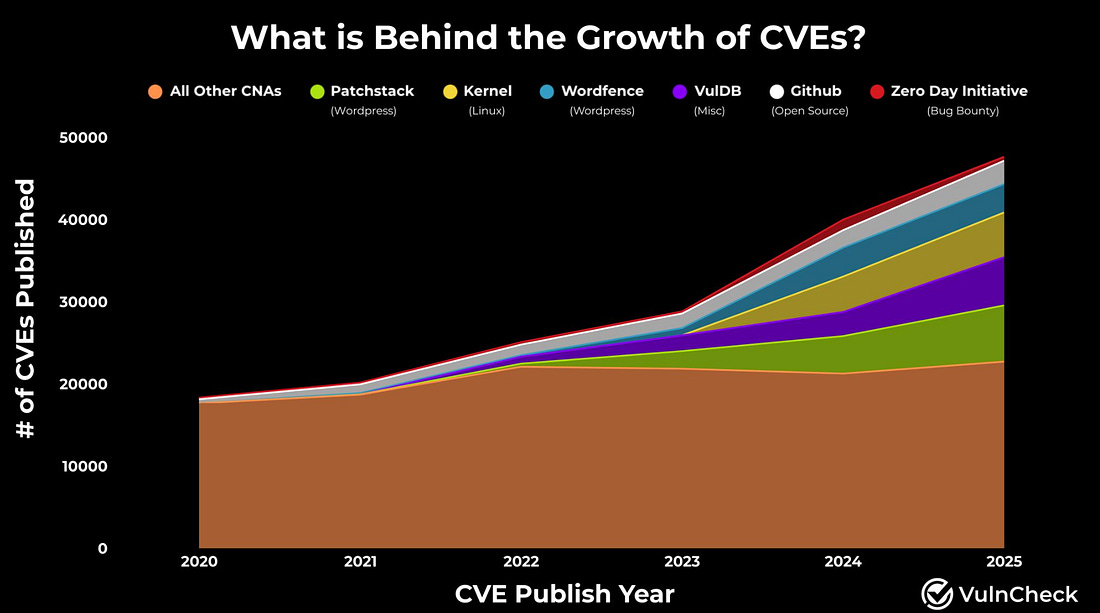
The same goes for scanners, from networks, to agent-based sensors, legacy hardware, API-based scanning, cloud environments and more. Customers want full not partial coverage when it comes to understanding their vulnerability footprint. This means new startups may have flashy and promising capabilities, but they lack comprehensive coverage and depth that most enterprises simply must have when it comes to VulnMgt. What’s Behind the Growth of CVE’s?Every year we tend to look at the raw number of CVE growth and stand in amazement, knowing we’re already struggling to keep up with vulnerability remediation and it is only getting worse. But, what’s actually behind the CVE growth? My friend Patrick Garrity of VulnCheck provides a great breakdown in a recent post of his. While it is true that the raw number of CVE’s is going up YoY, the truth is much of the growth is being driven by a small handful of CNA’s as he shows below: This isn’t to say that CVE growth isn’t a challenge, and in fact, I anticipate the rise of AI-driven development and vibe coding may lead to even more exponential growth, albeit it will be difficult to measure at the NVD level, given they don’t often know how the code was developed. All that said, it is helpful to see that a handful of CNAs often have an outsized impact on CVE growth annually. Resilient Cyber is free today. But if you enjoyed this post, you can tell Resilient Cyber that their writing is valuable by pledging a future subscription. You won't be charged unless they enable payments. |
Similar newsletters
There are other similar shared emails that you might be interested in: