OPERATION FROSTBYTE - Snowflake GOAT
- Chris Hughes from Resilient Cyber <resilientcyber+resilient-cyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
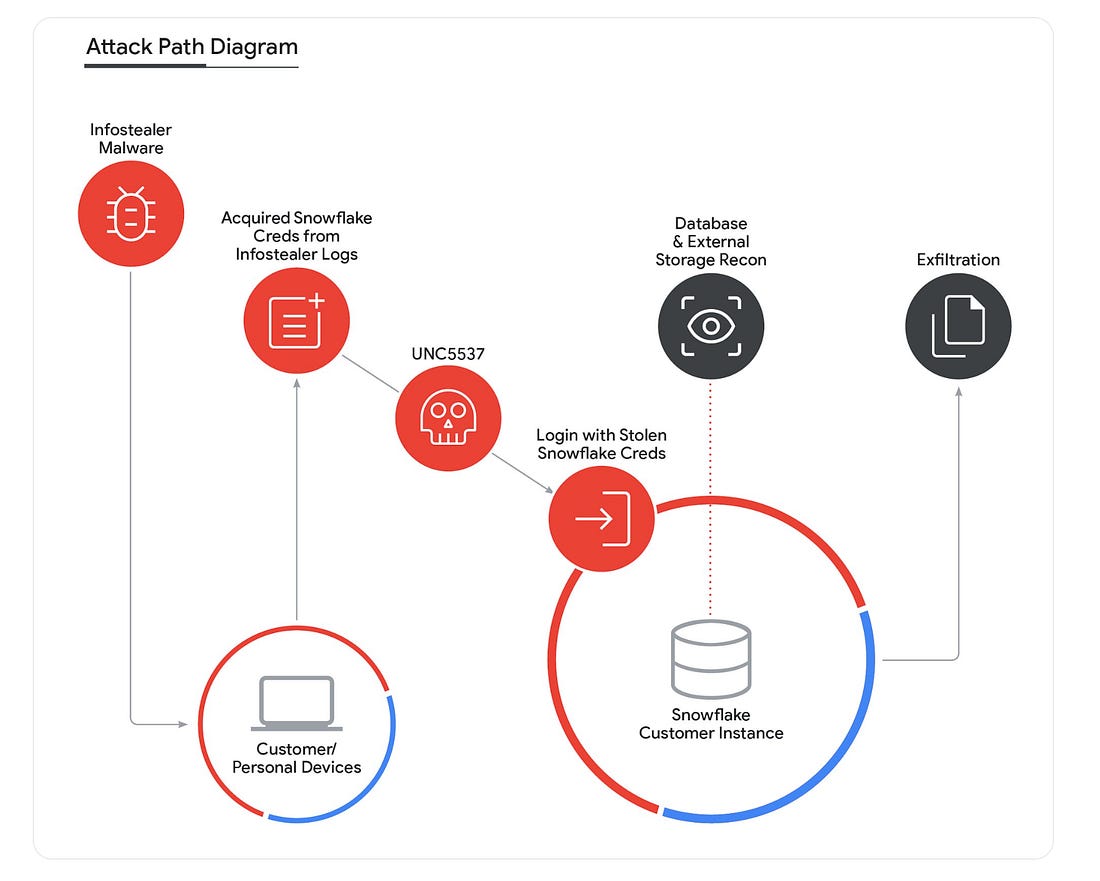
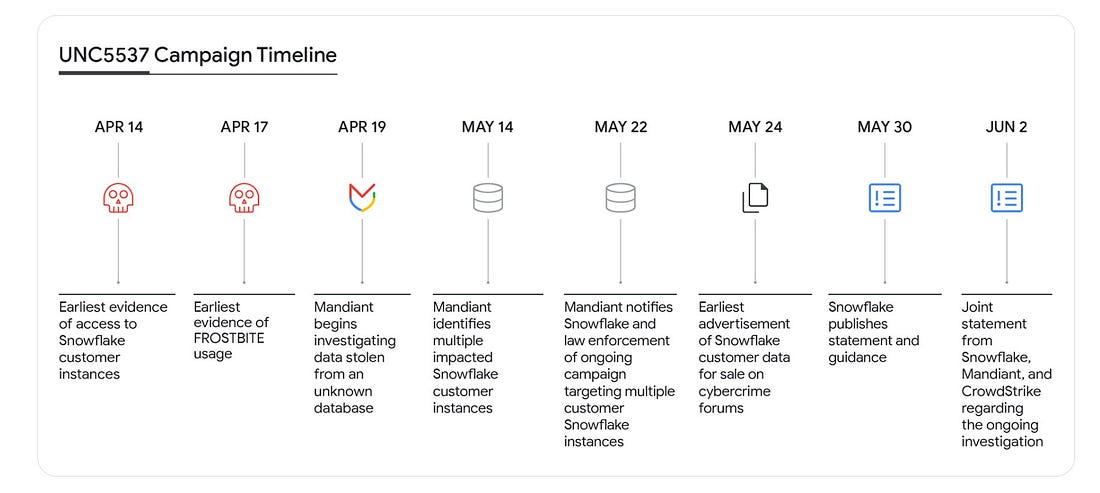
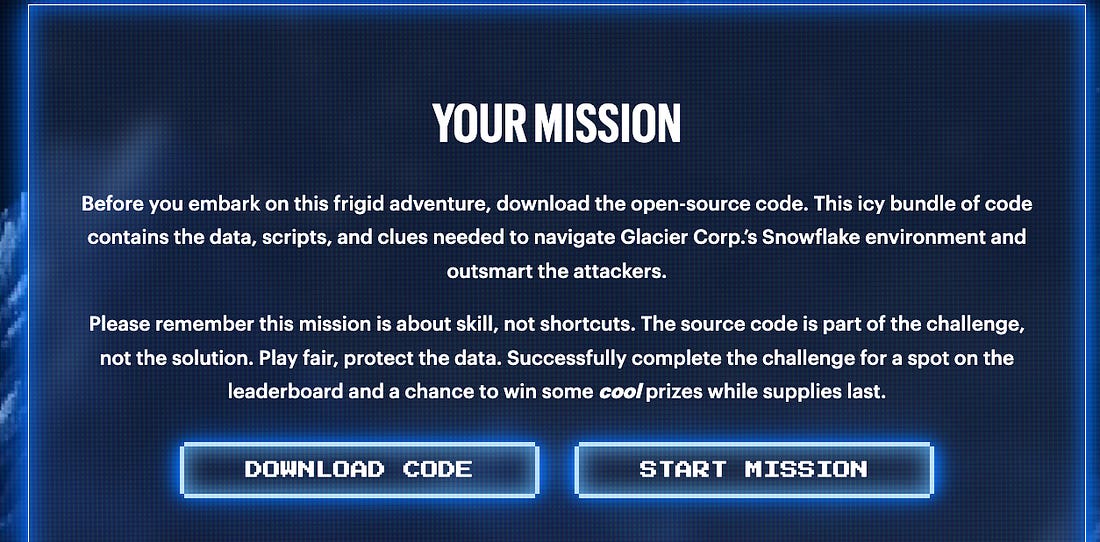
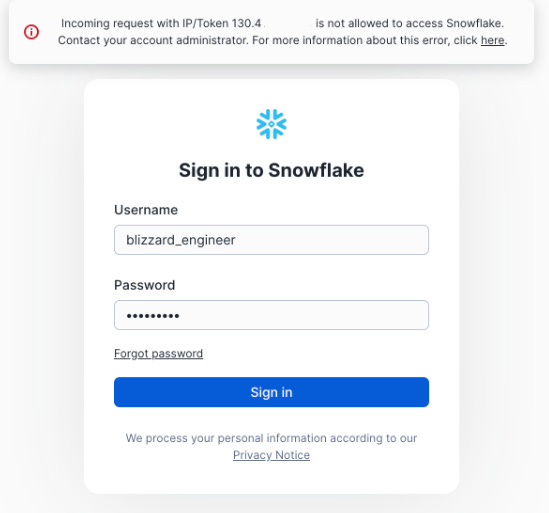
OPERATION FROSTBYTE - Snowflake GOATChecking out Varonis' Frostbyte - An Intentionally Misconfigured Snowflake Learning Resource for the CommunityIf you’ve been paying attention to cybersecurity over the past 12 months, you’ve inevitably heard about the Snowflake incident in 2024. It impacted hundreds of Snowflake customers, including big names such as AT&T and Ticketmaster, and involved extortion attempts by those who were impacted. The incident involved stolen credentials via an infostealer malware that could be used to access customers’ Snowflake instances. The Varonis Threat Labs team set out to put together some of the most comprehensive and detailed information related to the incident, including helpful diagrams such as the one below: Mandiant stated the stolen credentials dated as far back as 2020 and allowed the threat actors to gain access to the affected customer accounts and even export significant amounts of customer data from the impacted customer Snowflake instances, which led to subsequent extortion attempts, threatening to sell the data to cybercriminals etc. The incident also led to much discussion among the community about the fundamental shared responsibility in the cloud, including for SaaS providers and customers, and the importance of safe configurations and security controls within their instances of SaaS environments. To say SaaS configurations, including those of leading platforms and providers such as Snowflake, are complex would be putting it lightly. That’s why it’s awesome to see industry leader Varonis launch Operation Frostbyte—the first Snowflake GOAT. In this intentionally misconfigured environment, practitioners can tinker, test, and learn how to properly secure their Snowflake environments and keep sensitive data safe. It’s often said that bank robbers target banks because that’s where the money is, and it can be said that malicious actors target platforms such as Snowflake, where the enterprise data is. This may be sensitive information such as PII/PHI, financial information, enterprise credentials, and even security data for use cases like security data lakes. How Varonis approached building Snowflake GOATThere are various intentionally vulnerable technologies, products, and environments out there as the security industry realizes how proper a lab environment can be for educating security practitioners and offering them an opportunity to get hands-on. The Varonis team set out to build realistic attack paths and scenarios, such as excessive permissions that can allow privilege escalation and potential lateral movement into other sensitive data. They built Snowflake GOAT with practitioners in mind, whether it is red teams looking to sharpen their saw, defenders looking to better understand the potential risks of their enterprise Snowflake implementations, or others. It offers opportunities for both offensive and defensive cyber operators. They are even hosting a DEF CON workshop to empower the community to kick the tires, hosting a capture the flag (CTF) event where folks can play along, have fun, and see how they fare with exploiting the Snowflake implementations. Getting GoingVaronis took a fun approach as well, with a video game-themed implementation. They also leaned into the mantra of open source. Rather than hosting the game in a central location everyone must use, they provide the code via open source, allowing folks to download the data, scripts, and clues they need to participate in Snowflake GOAT. A users environments are provisioned via Terraform, making them declarative and repeatable, with users able to both quickly stand up and tear down testing and learning environments of the intentionally misconfigured Snowflake implementation. You also have an opportunity to get hands-on with the data in Snowflake, given it is the core value of the Snowflake platform and generally what attackers are after, and what defenders need to prevent against. Organizations can download the code and spin up a vulnerable/misconfigured Snowflake instance to easily test, learn, and develop defensive capabilities for their Snowflake instances. This represents an awesome resource for the community. It lets both defenders and offensive security practitioners use it, provide feedback, and even develop different scenarios to prevent future Snowflake incidents. So dive in, roll your sleeves up, get your hands dirty, and learn how to protect your organizations from risks associated with Snowflake today! Resilient Cyber is free today. But if you enjoyed this post, you can tell Resilient Cyber that their writing is valuable by pledging a future subscription. You won't be charged unless they enable payments. |
Similar newsletters
There are other similar shared emails that you might be interested in: