Resilient Cyber Newsletter #36
- Chris Hughes from Resilient Cyber <resilientcyber+resilient-cyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
Resilient Cyber Newsletter #36State of the CISO & Security Budgets, GenAI Red Teaming, AI Developer Evolution, CVSS Enrichment, & OWASP Threat and Safeguard Matrix (TaSM)Welcome!Welcome to issue #36 of the Resilient Cyber Newsletter. We’re back with another great collection of discussions, articles, and resources across security. We continue to see disruption across the U.S. Federal tech landscape from CISA to USDS. We discuss the state of CISO and security budgets, walk through the 3 CISO archetypes defined by IANS, and dive into resources from OWASP and others in the community around AppSec. So, let’s get to it! Interested in sponsoring an issue of Resilient Cyber? This includes reaching over 30,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives Reach out below!
Cyber Leadership & Market DynamicsCISO’s, Security Budgets & CareersIn this episode of Resilient Cyber, we sit down with Steve Martano, Partner in the cyber Security Practice at Artico Search, to discuss the recent IANS & Artico Search Publications on the 2025 State of the CISO, security budgets, and broader security career dynamics.  Steve and I touched on some great topics, including:
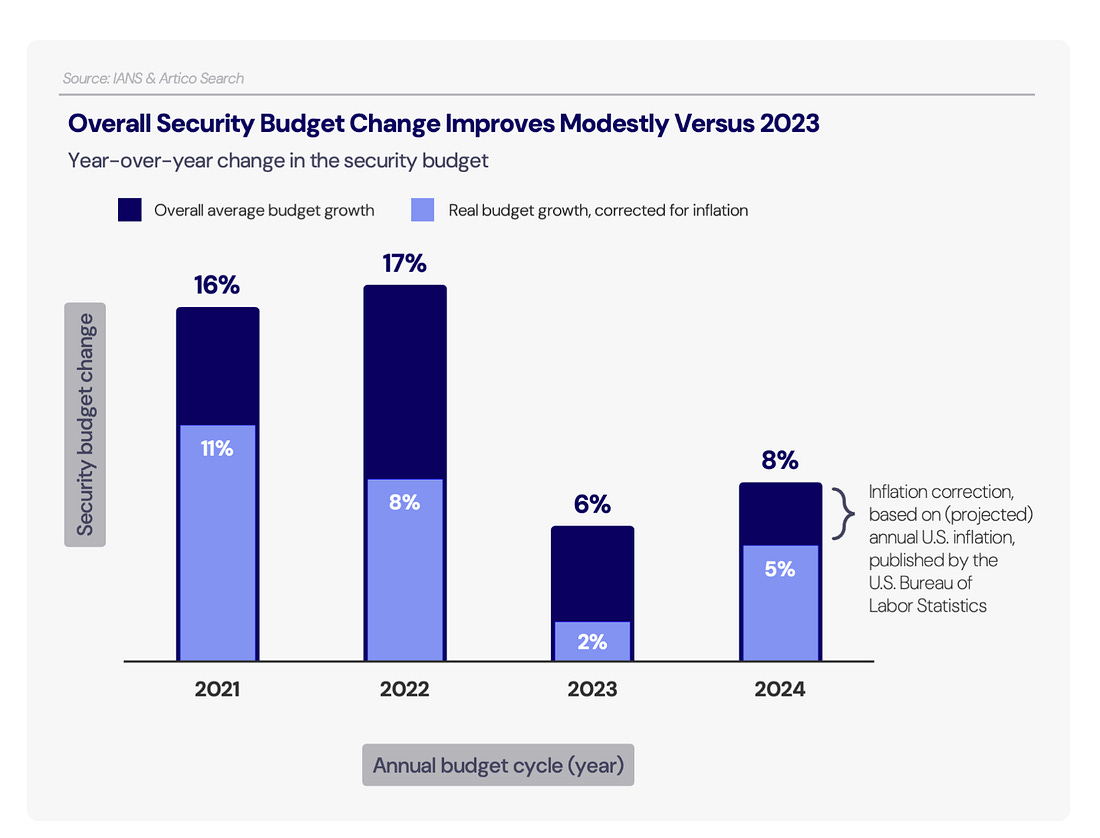
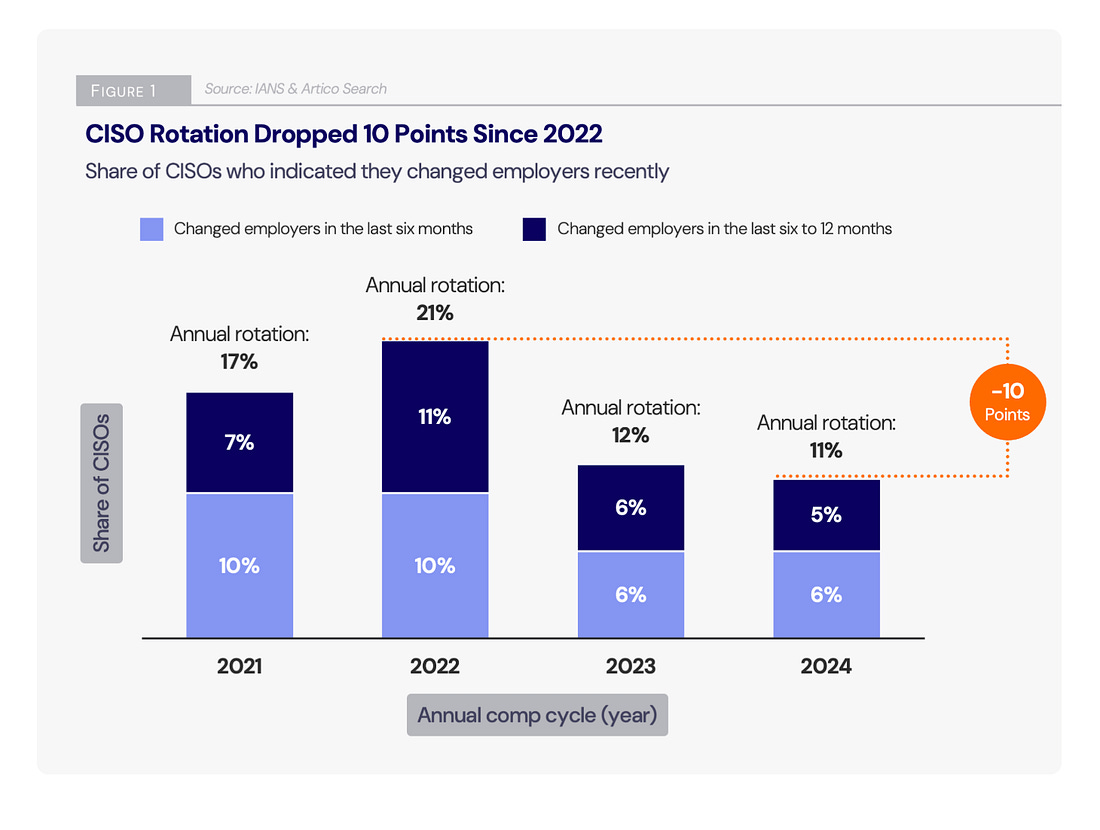
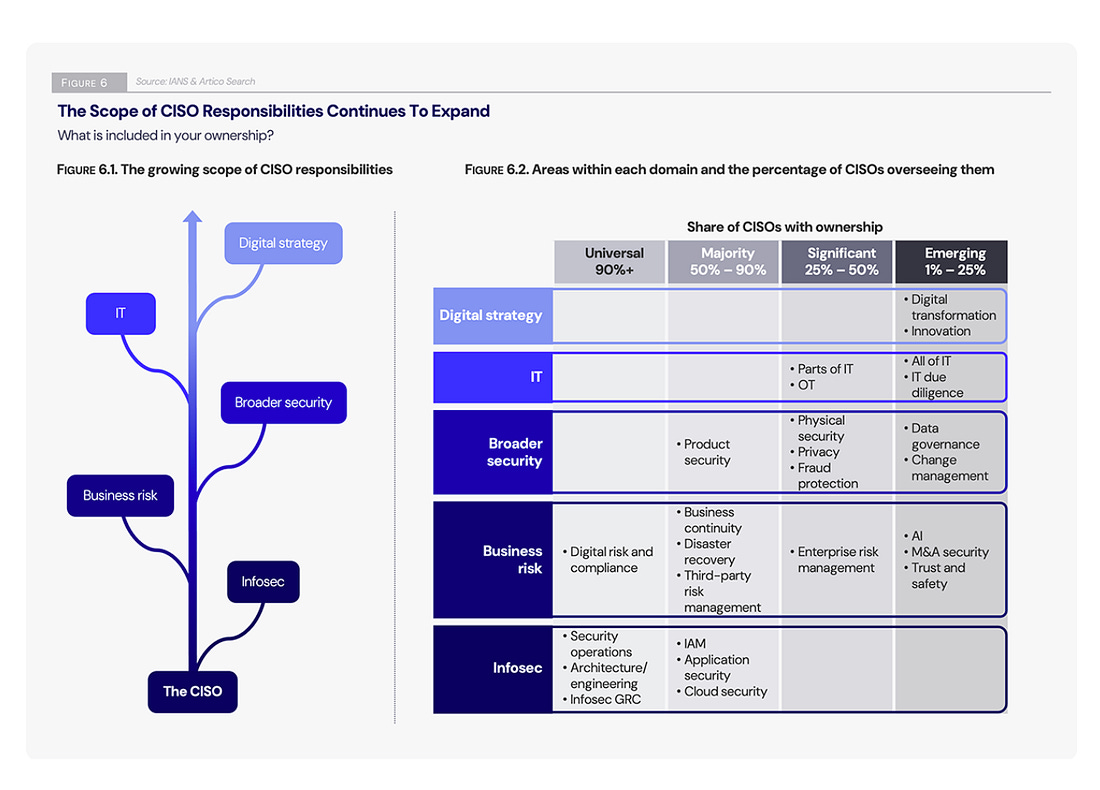
Below is a list of some of the great resources from IANS and Artico on various areas of interest for CISOs and Security leaders alike! Security Budget Trends and Benchmarks Report:CISO Compensation Trends & Benchmarks:2025 State of the CISO Report:Cybersecurity Leadership & Organization Trends:Strategic? Functional? Tactical? Which type of CISO are you?Speaking of the various categorizations of CISOs, CSO Online recently ran an article discussing the CISO archetypes and the way CISOs fit (or not) into the roles depending on the organziation. A misfit scenario can be a negative experience for both the CISO, and the organization. The article draws on the IANS report for reference and discusses how some CISOs can move between the archetypes depending on the needs of the day and organization, while others tend to thrive in a specific category. There is nuance too, depending on the organizations size and maturity the CISO may not have the luxury of being strategic, and in fact, may be juggling multiple roles themselves with little to no resources or supporting cast. This is something Steve and I dove into in the conversation above, for those who want to tune in and learn more. CISA and USDS Expertise Hiring OpportunityGiven the Federal trend around layoffs, RIF’s, resignations and more, we’ve seen a lot of incredibly talented engineering, security and technology professionals actively seeking new roles. I wanted to highlight a couple of valuable resources below, one for former CISA folks actively seeking roles, and the other for USDS. These are great opportunities to hire incredibly mission driven and talented technology professionals! Managing the Emotional Toll Cybersecurity Incidents Can Take on Your TeamWhen we think of security incidents it is common to think of impacts such as reputational harm, stock price, financial consequences, ransom and more. However, another often undiscussed toll is that of the emotional impact on the cybersecurity team dealing with the incident. This article discusses that emotional impact, as well as how it can end up leading to financial impacts on the organziation such as decreased performance due to low morale and attrition among the team. The UK Undermines User PrivacyIt's been reported that Apple has pulled its iCloud end-to-end encryption feature for UK users after the government demanded a backdoor. What's ironic is that Western nations, on the one hand, get on their soapboxes and criticize authoritarian nations and how citizens are treated. Cyber Command 2.0While there are many differences between the current and previous U.S. Presidential administrations, there is also some alignment. One area is a Biden-era plan to revamp U.S. Cyber Command. This includes compiling and then implementing a list of authorities that Cyber Command would need to be more effective and also eliminating or reducing regulations that hinder its ability to conduct cyber operations. This also seems to align with speculation that has been swirling about a forthcoming cybersecurity executive order (EO) that is poised to focus on increasing the U.S.’s ability to be more effective at offensive cyber operations, while previous cyber EO’s have heavily focused on defense. Additional projected focus areas for Cyber Command 2.0 include:
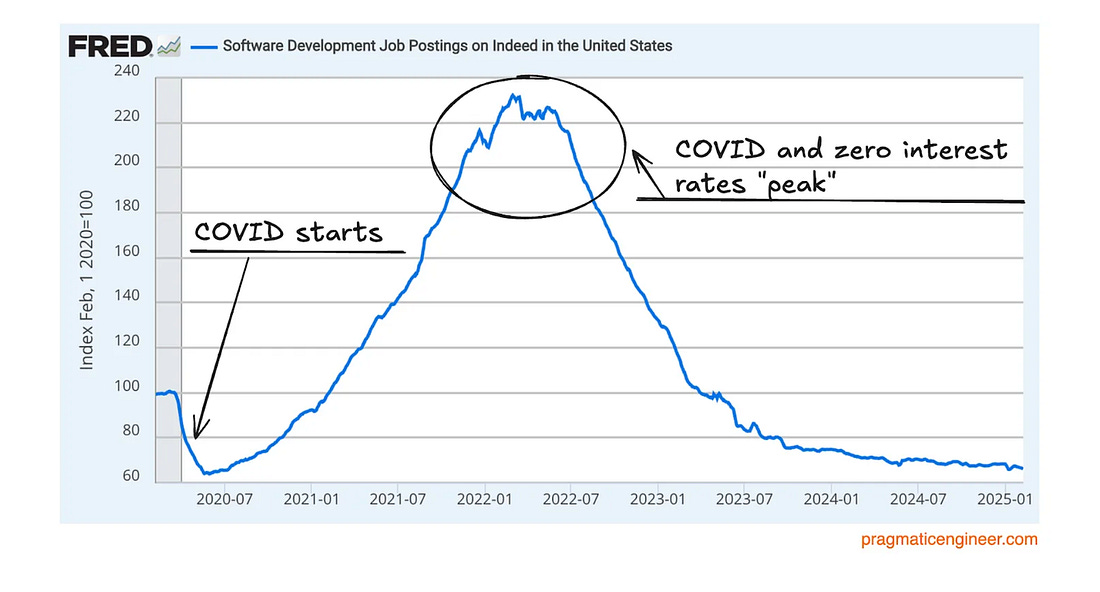
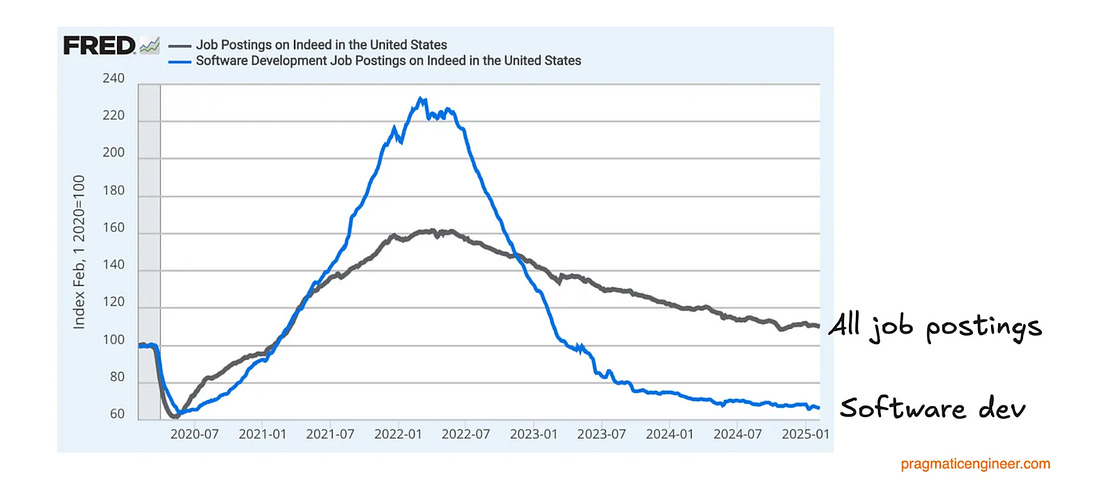
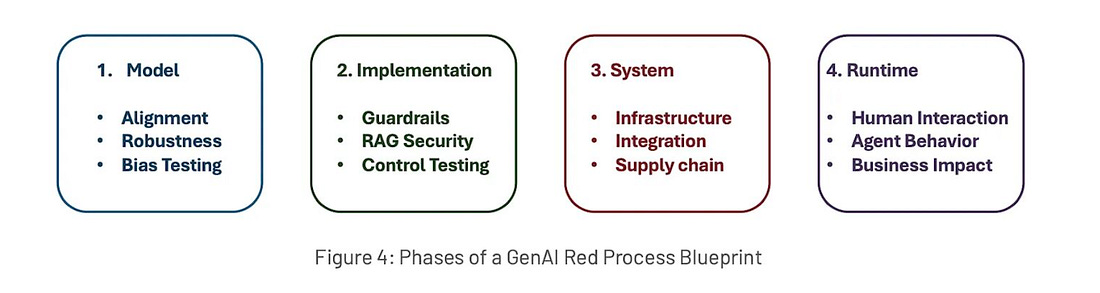
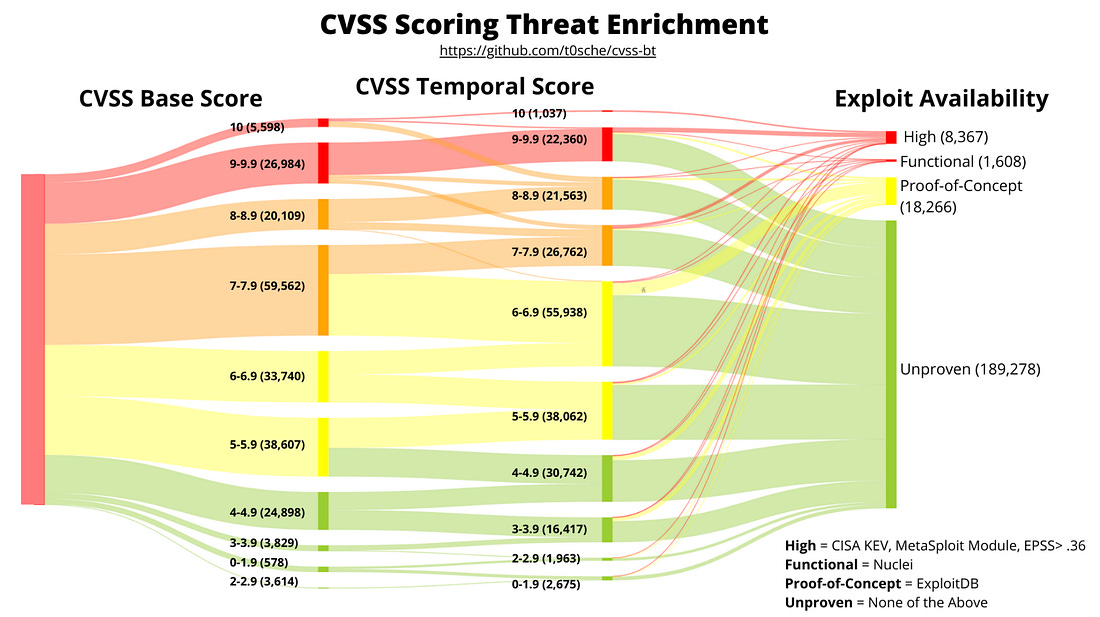
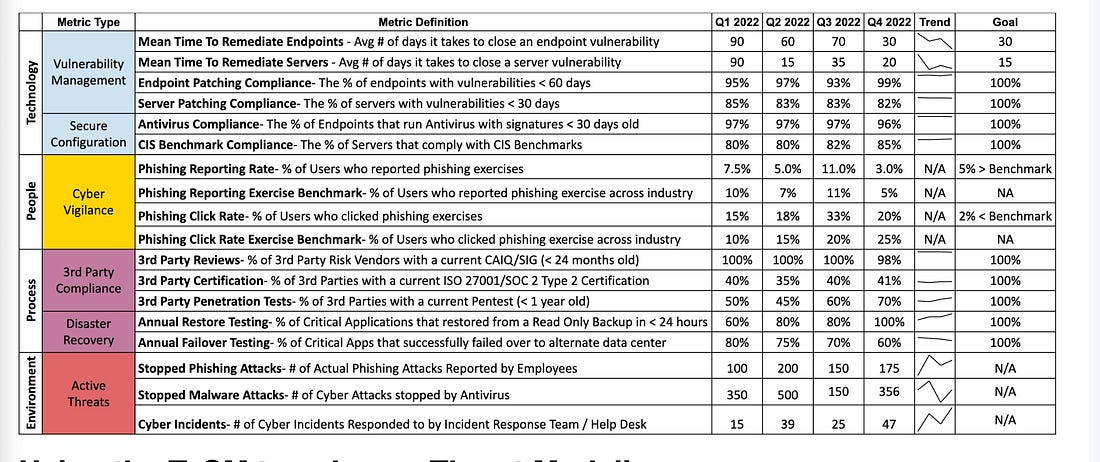
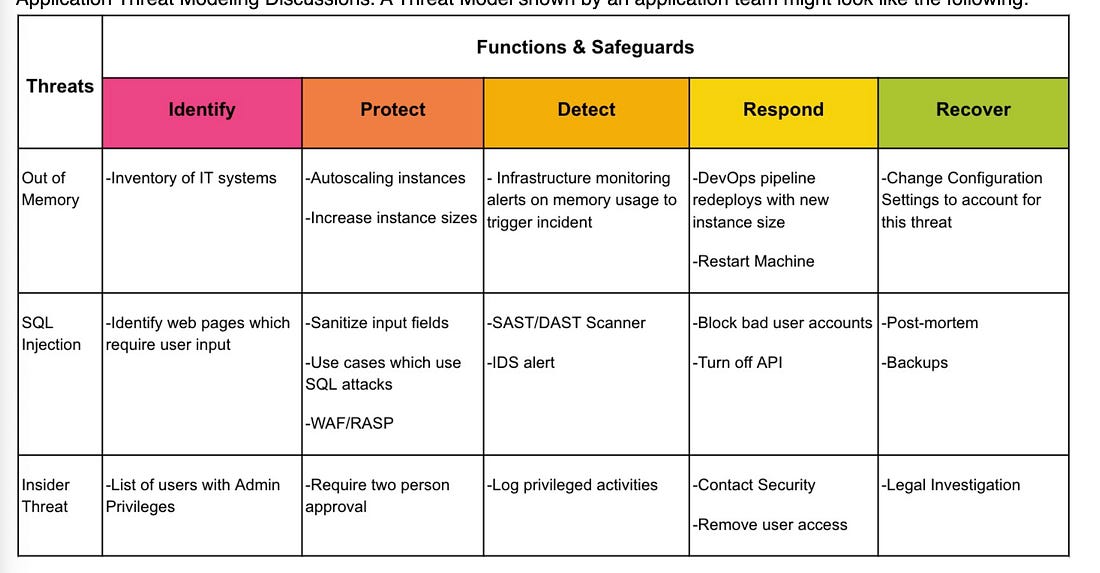
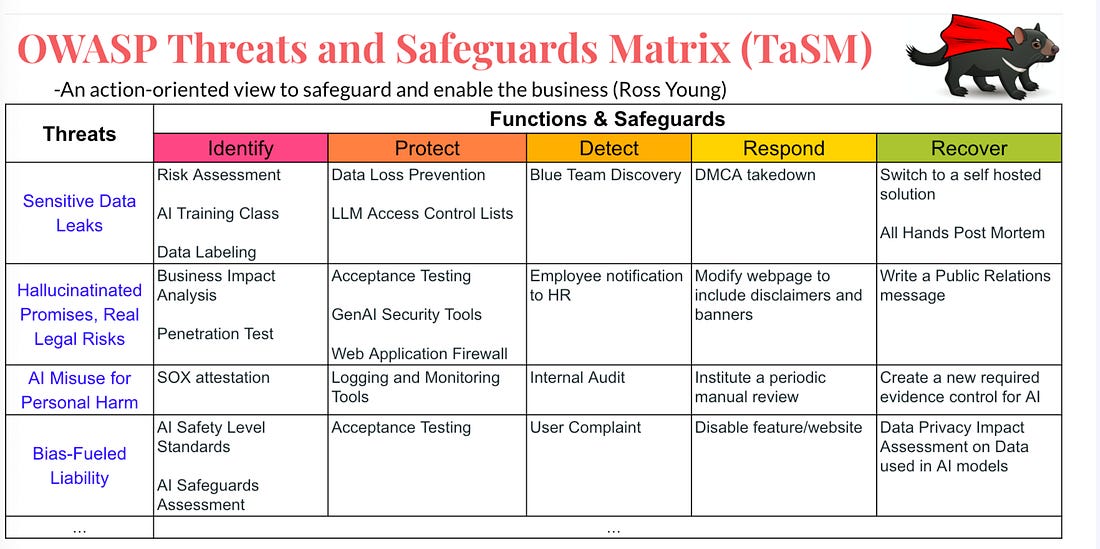
Think being a CISO of a cybersecurity vendor is easy? Think againThe CISO role can differ depending on the industry, organization type and size, and more. One of the unique examples includes being a CISO at a cybersecurity vendor. This particular role is often not viewed as being a “real” CISO, as described by Tyler Farr in this piece on CSO online. That is because many view the role as more sales-oriented than really security-focused and securing an organization against cyber risks. However, as Tyler points out, being a CISO for a security vendor often comes with all of the internal security responsibilities of a traditional organization and increased accountability and visibility since security sales run on trust. If you have an incident as a vendor, you can lose credibility and find it more difficult to gain and keep customers’ trust. As Tyler says in this piece, “In cybersecurity, the product is a promise.” Customers want to know how the product is secured and that it promises to protect them and their data and help reduce risk. As Tyler states, security vendor CISOs are a bridge to customer trust. I will add from my perspective, depending on the size of the vendor, the CISO may be focused strictly on internal security practices, while there may be one or more “Field CISOs” who function as that bridge to trust and are out in the “field” engaging with customers and functioning in more of a sales capacity, while the CISO may be focused on internal organizational and product security, but this really varies and depends on the vendor’s size and maturity. AIAI is Prompting an Evolution, not an Extinction, for CodersWe often hear about the disruption that AI will cause among the workforce, including for Developers. In a bit of a play on the word “prompt” this piece from NYT makes the case that GenAI and AI-driven coding tools are leading to an evolution of the way Developers work rather than an extinction. As the saying goes, AI won’t take your job, but someone using AI will. The piece discusses how many Developers are now regularly working with copilot coding tools and couldn’t imagine not doing so for everything from development, testing, integration and more. The article covers the fundamental way AI is changing but not eliminating the way Developers work and the CEO of GitHub is quoted as saying how in the coming years 80-90% of the code written may be by AI, with many already saying it is saving them 4-5 hours a week if not more. Exampled cited include getting new Development team members up to speed, capturing documentation for code (something no one enjoys doing), and helping transition legacy code bases to new languages, which has potential when we look at the push to move to memory safe languages, such as Rust, which got a big push by CISA and others in 2024. There’s also discussion about the implications for Developers in terms of hiring, and it cites how the demand for junior Developers has weakened. There are additional sources citing this dip overall, such as Subtack’s leading outlet, The Pragmatic Engineer, who shared a piece showing Developer job listings have reached a five year low (see below): At first, it is easy to think this is specific to Developers, but as they show below, this coincides with an overall decline in postings as well, which isn’t surprising given we came out of the COVID era, ZIRP, and have faced persistent economic challenges in not just the U.S. but around the world. However, we can see that despite an overall decline in postings, Developers did indeed face a steeper and more drastic decline. In addition to the way AI is changing the way Developers work, I have been particularly interested in if the “productivity” boon of more code faster will equate to more vulnerabilities and an explosion of the digital attack surface, especially given LLM’s are trained on open source code bases which often include vulnerabilities. While the research is still maturing on this, right now it looks like that will be the case, making security, and leveraging AI for AppSec even more critical. GenAI Red TeamingRed Teaming is emphasized in leading AI security frameworks and requirements, from NIST's AI RMF to the EU's AI Act. Red Teaming is a longstanding cyber practice that identifies and mitigates risks against systems. US AI Safety Institute Could Face Big CutsMany U.S. Federal agencies are facing severe cuts and downsizing. Among those include the National Institute of Standards and Technology (NIST), home of the US AI Safety Institute. It is being reported that the organization may be targeted for deep layoffs, including “probationary” employees, who are in their first year or two on the job. This isn’t incredibly surprising given we’re seeing cuts across many agencies, and the latest AI EO which focused on innovation, American dominance and removing burdensome regulations, including the previous Biden AI EO, which focused on safety and security. AppSec, Vulnerability Management, and Supply Chain SecurityUnderstanding OWASP’s Top 10 List of Non-Human Identity Critical RisksNHI's remain one of the most discussed topics in the identity security space. This is especially true with the excitement around Agentic AI. CVSS Scoring Threat EnrichmentMany are painfully familiar with the Common Vulnerability Scoring System (CVSS) and its shortcomings. CVSS often gets a bad rep, and understandably so, as it has many challenges. Vintage Vulnerabilities and Critical InfrastructureSalt Typhoon was the name attributed to the threat actors that conducted the “largest breach of U.S. telecommunications” in 2024. It is evident that among the attack vectors, the group used a 7-year-old vulnerability in Cisco software/products. "The hackers, tied to Chinese intelligence, mostly gained access to Cisco devices by acquiring victim login information, but in a single case took advantage of a Cisco router flaw that has been publicly documented in the National Institute for Standards and Technology’s vulnerability database for seven years." OWASP Threat and Safeguard Matrix (TaSM)We often hear that cyber is in the business of revenue protection, but how do we put that into actions? The OWASP TaSM is one tool to help. It lets an organization overlay major threats across a matrix aligned with NIST’s Cybersecurity Framework (CSF) and build a security plan aligned with each function of CSF as well as align safeguards accordingly. Below is a notional example of TaSM with with example threats as well as functions and safeguards to address those threats. TaSM can also be used for metrics and measuring improvement, as well as enhancing threat modeling (shown in order below): TaSM even shows how it can be aligned with AI threats, such as below: TaSM is a very versatile framework and can be used for many purposes as seen below. It is led by my friend Ross Young, who’ve I’ve previously interviewed on Resilient Cyber, where he discussed all the ins and outs of How to Become a CISO  Resilient Cyber is free today. But if you enjoyed this post, you can tell Resilient Cyber that their writing is valuable by pledging a future subscription. You won't be charged unless they enable payments. |
Similar newsletters
There are other similar shared emails that you might be interested in: