Resilient Cyber Newsletter #76
- Chris Hughes from Resilient Cyber <resilientcyber@substack.com>
- Hidden Recipient <hidden@emailshot.io>
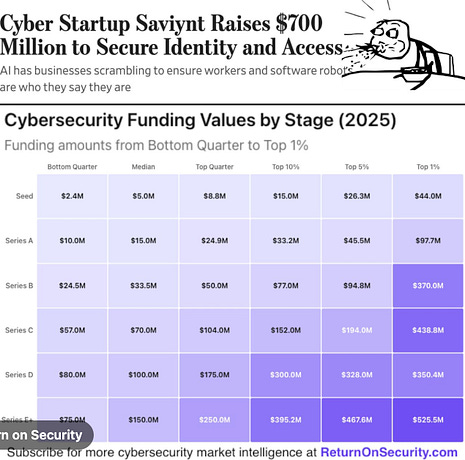
Resilient Cyber Newsletter #76Saviynt $700M Series B, AI Impacts Buy vs. Build, U.S. White House AI EO, State of GenAI in the Enterprise, OWASP Agentic AI Top 10, 20254 CWE Top 25 & Fixing the Broken VulnMgt EcosystemWelcomeWelcome to issue #76 of the Resilient Cyber Newsletter. We’re winding down a wild 2025, with a TON of M&A activity over the year, a lot of exciting advancements at the intersection of AI and Cybersecurity and a continuously challenging landscape around AppSec and incidents. I’ve truly enjoyed sharing my perspective with you all through the year and I’m excited about what 2026 holds! Personal Note:With the year coming to a close, I wanted to reflect a bit on what a journey the last few years have been professionally and personally. To say the last several years of professional growth and development have been a whirlwind would be an understatement. Interested in sponsoring an issue of Resilient Cyber? This includes reaching over 40,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives Reach out below! Cyber Leadership & Market DynamicsIdentity Management “Startup” Saviynt Closes $700M Series BIn one of the largest Series B rounds I’m aware of, Saviynt, who focuses on identity security caught headlines with a massive $700M round. KKR was the lead investor along with Sixth Street Growth, TenEleven and returning participants as well. In the announcement their CEO emphasized that:
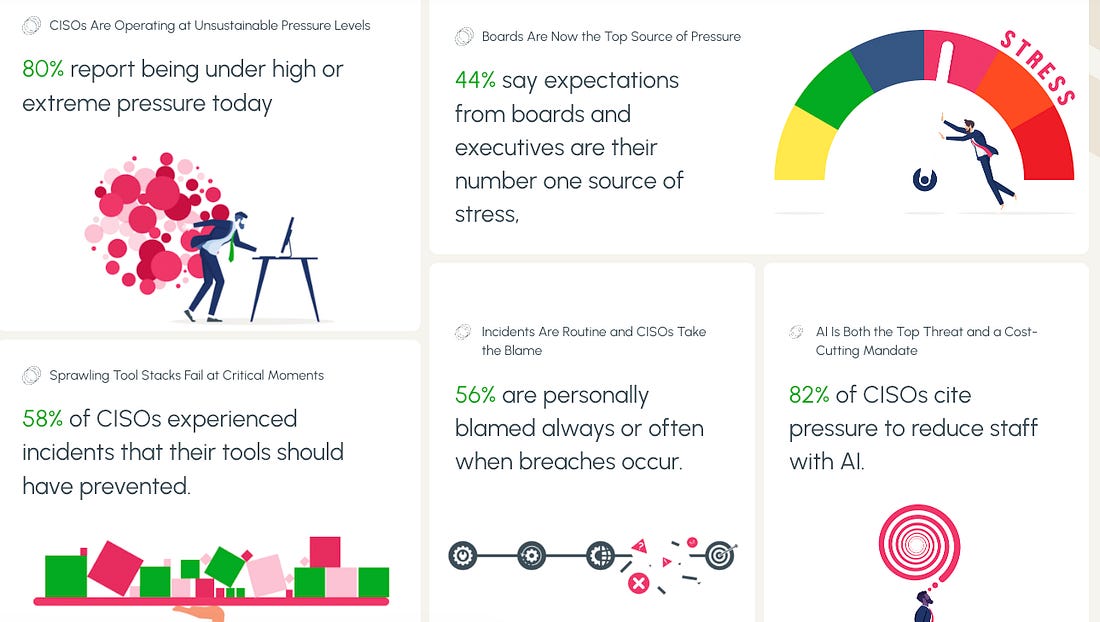
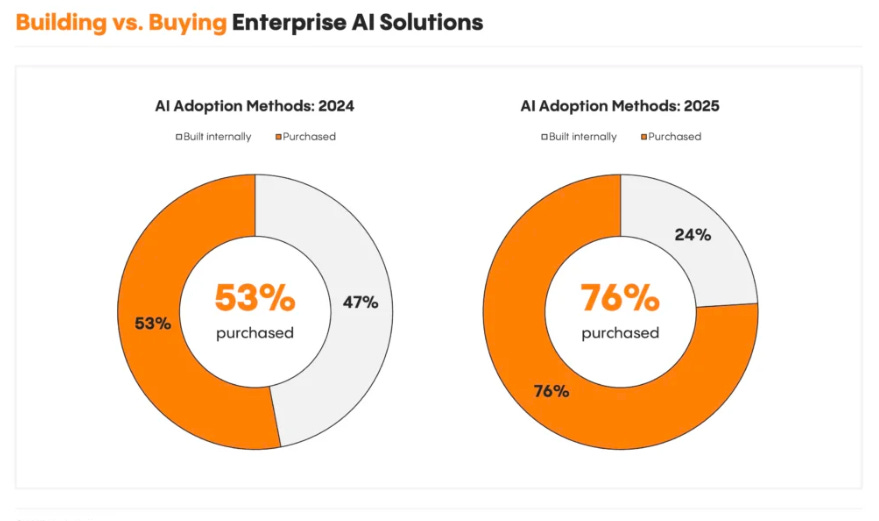
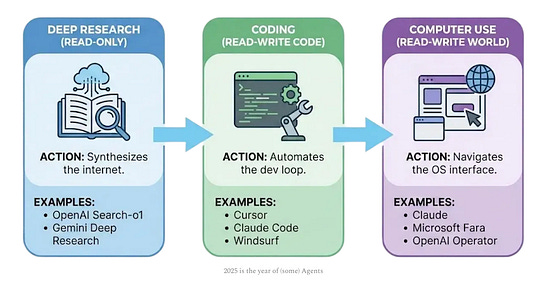
We continue to hear phrases such as “identity is the new perimeter”, and we’ve seen other massive moves in the Identity space this year, such as Veza being acquired by PANW as well. Safe to say, the identity security space is highly competitive and also densely populated. My friend Mike Privette of Return on Security (RoS) discussed the round in a recent LinkedIn post, explaining how it is one of the largest Series B rounds in cyber history at nearly 20x the 2025 median. As he explains, this is more of a PE round than tradition VC Series B, with KKR being the lead investor. While this example is an outlier and not the norm, Mike did note that t he median Series B in 2025 is up 12$ compared to 2024. 2025 CISO Pressure IndexIt’s common by now to hear a lot of discussions about the pressure CISOs and security leaders face. However, there often aren’t specific surveys and studies on the topic, which is why I found this resource from Nagomi interesting. They found that CISOs said: Be sure to check out the full report! Build vs. Buy is Dead - AI Just Killed ItWe continue to see revived conversations about Build vs. Buy in the age of AI. I recently had shared an excellent article from Caleb Sima, where he laid out how AI is going to lead to the rise of “zombie tools”, where people chasing resume driven development, or being short sighted about the long tail of product sustainment look to build their own internal products versus buying them leads to a sprawl of orphaned zombie tools. This recent VentureBeat piece that my friend Chenxi Wang shared with me digs into the topic too. It frames scenarios where individuals within the org can quickly spin up prototypes or versions of products quickly with agentic coding tools. The piece discusses the “old framework”, where organizations grappled with the decision to Build or Buy, with building being expensive and taxing on the existing technical talent. Now, with the rise of AI coding tools, many feel they can take on building due to a collapsing of the cost and complexity of doing so. What I liked with this piece is it lays out a new potential sequence, as seen below:
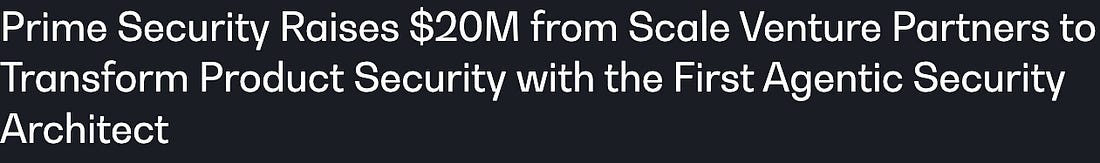
This framing is a good way to think of it, because it recognizes that Building is a long term strategic investment, but doing quick efforts to build, iterate and tinker before determining what you need and then determining what to buy is a great way to drive better decisions when you finally do commit to making a procurement, while also not framing AI developed prototypes as longterm replacements for commercial grade software products or platform. This gets to the heart of the matter, that most organizations don’t even know what they need to begin with - but AI may let them prototype to figure it out. Transforming Product Security with the First Agentic Security ArchitectContinuing the momentum in the product security space, Prime Security recently announced their $20M Series A, led by Scale Venture Partners along with Foundation Capital and others. Prime is an interesting player, focusing on moving Secure-by-Design from theory to tactic and making it actionable by living and breathing in the space and data systems are actually designed in to provide critical context before systems are ever developed or deployed. Defending Your Cyber Systems and Your Mental Attack Surface with Chris Hughes When your firewall forgets to buckle up, the crash doesn’t happen in the network first, it happens in your blindspots. In this episode of Hacker Valley Studio, I got to join host Ron Eddings. I attempted to help reframe vulnerability work as exposure management, connect technical risk to human resilience, and broke down the scoring and runtime tools security teams actually need today. I also provided clear takeaways on EPSS, reachability analysis, ADR, AI’s double-edged role, and the one habits I swear by. This episode fuses attack-surface reality with mental-attack-surface strategy so you walk away with both tactical moves and daily practices that protect systems and people. Offensive Security Takes Center Stage in the AI EraMost experienced security leaders openly admit the way we assess systems and posture is broken. It historically involved snapshot-in-time assessments, paper-based compliance and other inefficient methods. While we move in months, systems change in minutes and attackers exploit what is actually running in production (a fact that is also leading to the rise of new categories such as Application Detection & Response). In this piece on CSO, various CISO’s and security leaders weigh in on the emphasis they’re playing on Offensive Security (OffSec) and the importance of iterative real-time assessment of their production environments. AI is driving that even more, both from the perspective of attackers leveraging it, as well as innovative companies leveraging AI and Agents to bring ongoing Pen Testing and OffSec to reality. Good examples include Horizon3, XBOW and others. With the evolution of AI and Agents, we have the potential to take historically cumbersome activities such as Threat Modeling, Pen Testing and Purple Teaming and make them iterative and ongoing, as part of the SDLC, and if compute and inference costs continue to collapse, we will see them become even more economically practical to pursue via AI as well. Trouble for Microsoft When It Comes to Agentic AI?This piece states that Microsoft has cut its sales targets for its Agentic AI Copilot software significantly, potentially up to 50% as it struggles to get interest from customers. The piece also states it is falling behind others such as ChatGPT and Google’s Gemini. ServiceNow (SNOW) To Acquire Armis for $7 BillionNews recently broke that industry giant SNOW is in talks to acquire Armis for a potential $7 billion deal. Armis was last valued at $6.1 billion. Armis focuses on securing and managing connected devices and just raised $435 million in a funding round in recent months, and had discussed their IPO ambitions openly. As the CNC article notes, while many may have IPO ambitions, more often than not, most cyber companies opt to stay in the private market given the choppiness of the public markets, as well as increased scrutiny it brings. This news comes as SNOW was recently announced to be acquiring identity security company Veza as well, demonstrating SNOW is on an acquisition spree, focusing on critical areas of cyber from devices and endpoints to identity. The Container Vulnerability Ecosystem Stays HotWhile the secure base images and container security ecosystem has been dominated by teams such as Chainguard, in recent years we’ve seen several existing and new players enter the field, further validating this category. The latest example comes from Echo, who announced going from $0-$50M Series A in a LinkedIn post from their Cofounder & CEO Eilon Elhadad. The team brings strong venture support too from players such as Notable, Hyperwise, SentinelOne and SVCI. AIThe White House Drops an EO for a U.S. National AI Regulatory FrameworkI’ve been sharing a bit lately about the ongoing debate about State vs. Federal AI regulation here in the U.S. In the absence of a Federal regulatory framework for AI, many states have rolled out their own AI regulations and requirements. Many, including the current administration argue it is going to hinder innovation, be too costly and cumbersome for industry and stifle the U.S. ability to compete internationally both economically and from a national security perspective. This latest EO titled “Ensuring a National Policy Framework for AI” looks to address the lack of a Federal level AI regulation framework and also block state level efforts that may impede overarching Federal goals. The U.S. Federal government (and the tech sector) are looking to avoid a patchwork quilt of countless state level AI regulations that will be costly and problematic to navigate and comply with and could slow down the U.S. raise to out innovate China in particular when it comes to AI. The EO calls for a “minimally burdensome” national policy framework for AI. It also stresses the need to be able to innovate:
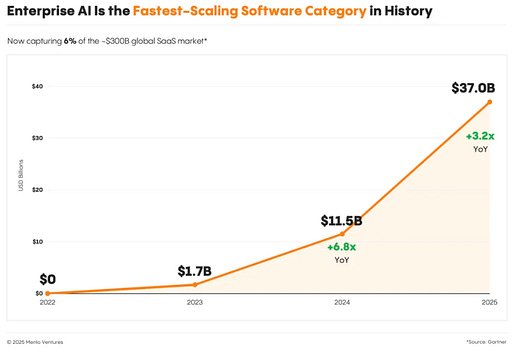
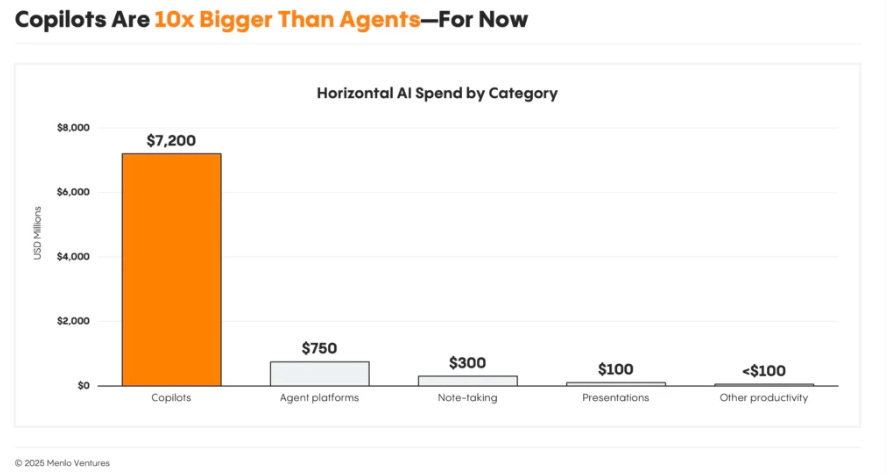
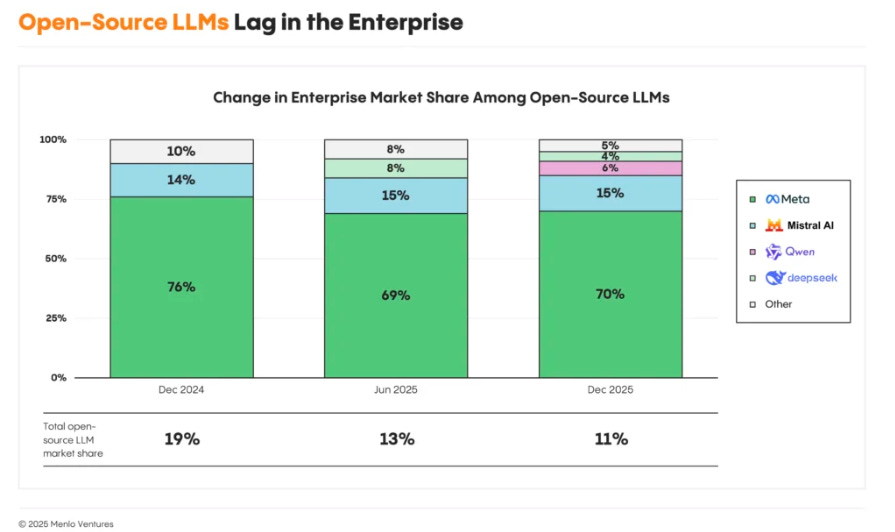
The EO does allow for various State AI laws too though, specifically in areas dealing with child safety, State procurement etc. AI Eats the WorldI inevitably find myself consuming more long form video and audio content as I am learning and staying up to date on the industry, cyber and AI. Few do macro analysis related to trends better than Benedict Evans. In this excellent talk with a16z Benedict dives into all things AI, speculation around bubbles, where AI is or isn’t generating ROI, its role as the next platform shift and much more.  2025 State of GenAI in the EnterpriseAI is experiencing adoption and usage at an unprecedented pace, and the latest Menlo Ventures 2025 State of GenAI in the Enterprise Report lays out how. ↳ Coding continues to dominate the department AI spending, pulling down $4 billion or 55% of ALL department AI spend in 2025 (this has AppSec implications!), most of this is focused on Copilots by poised to shift to Agents as they mature. Unpacking the OWASP Top 10 For Agentic AIRecently I shared how the OWASP GenAI Security Project released the first official Top 10 for Agentic AI. We’re entering what many suspect will be the decade of AI agents, with Agentic AI poised to disrupt nearly every industry and vertical. We continue to see Agentic AI as one of the most discussed and exciting areas of the AI evolution, with potential across nearly every industry and vertical, including Cybersecurity. Zenity Expands AI Security with Incident Intelligence, Agentic Browser Support and New Open Source ToolThe team at Zenity continues to impress me with their rapid innovations in the Agentic AI Security space. Building on their industry leading platform and research that I routinely find helpful, they announced a trio of capabilities recently:
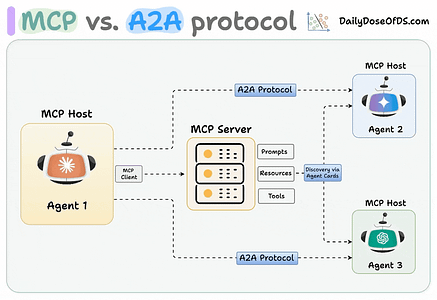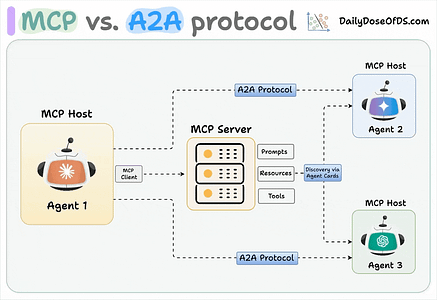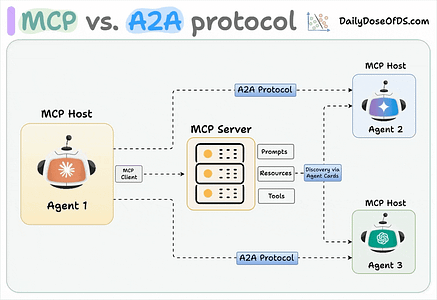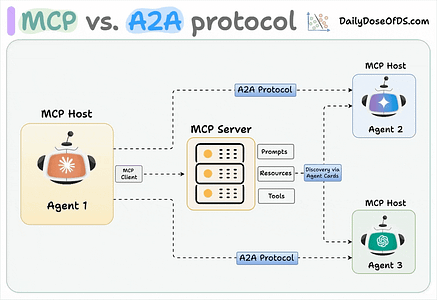
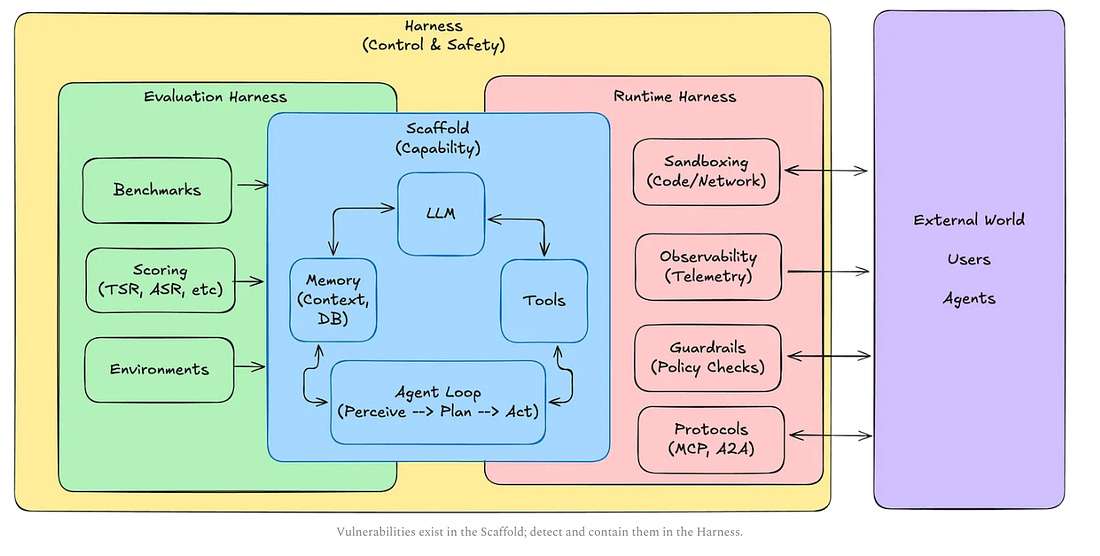
Jason Stanley, who leads AI Research Deployment for ServiceNow actually had an excellent blog titled “Incident Agents, Pattern Cards, and the Broken Flow from AI Failures to Defenses” where he used Zenity’s intelligence layer as an example of addressing gaps when it comes to Agentic AI for cybersecurity defense and incident use cases. Be sure to give Jason Stanley a follow on Substack. Securing AI Agents with Cisco’s Open Source A2A ScannerWhile MCP has dominated a lot of the discussion about protocols supporting Agentic AI in 2025, another critical protocol is A2A, which focuses on inter-agent communications, while MCP is more so focused on tool use and resources. Cisco defines A2A as:
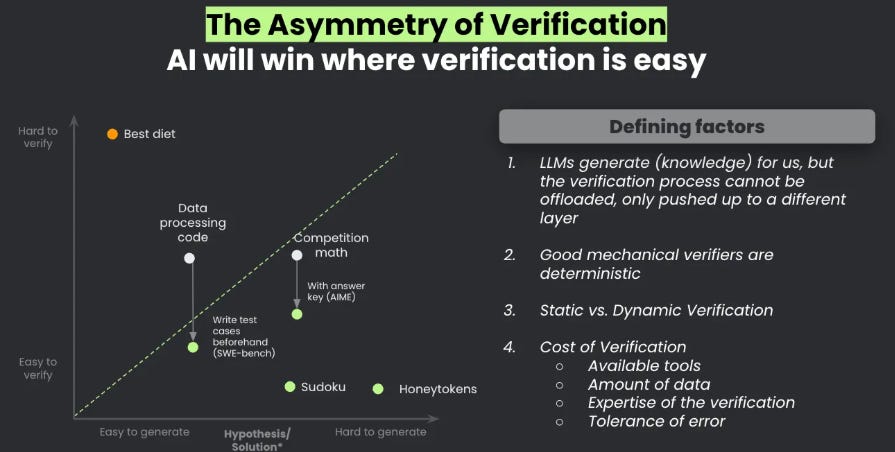
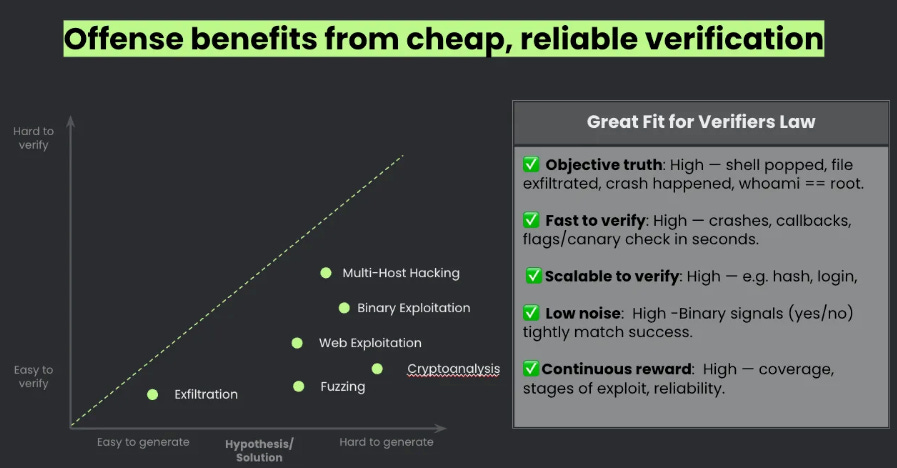
The team at Cisco, including my friend Vineeth Sai Narajala, recently announced their open source A2A scanner which can validate agent identities and inspect their communications for threats. I’ve had Vineeth on the Resilient Cyber Show in the past to dive into all things AI, Agents and Protocols.  Your AI Agent Just Got PwnedI recently ran across Matthew Maisel‘s incredible blog titled “Your AI Agent Just Got Pwned: A Security Engineer’s Guide to Building Trustworthy Autonomous Systems”. It’s an incredibly detailed piece, diving into the control and safety of agentic systems and the nuances on everything from evaluations to runtime. AI Agents and the Core of IAM: Key Takeaways from the Gartner IAM Summit 2025Identity continues to dominate a lot of the discussion in cybersecurity, with major acquisitions, new entrants and strategic moves by large players. This is true in the Agentic AI space too, and Gartner recently hosted a 2025 IAM Summit. Astrix’s Field CTO Jonathan Sander shares the key takeaways in a helpful blog. Jonathan emphasized that the key theme of the event was still that Identity is the core of everything, but the new twist this year of AI Agents, which makes sense, given it is a theme that has dominated many conversations beyond just Identity in 2025. The conversations also included the need to map connections between the low level technical elements of IAM, to broader business functions and value. Winning the AI Cyber Race: Verifiability is All You NeedWe continue to see a lot of theoretical and not so theoretical discussions about AI in Cyber, and who is or will win, defenders or attackers. A critical part of the challenge that often gets neglected is that AI thrives on verifiability. As Sergej Epp lays out in an excellent article, attackers often have it much easier when it comes to verifiability. Did you get a shell or not? Did you compromise a host or not? Did you exploit a vulnerability or not? Defenders? Not so much We’re often drowning in massive noisy data, thousands and millions of alerts, notifications, false positives and logs. As Sergej says:
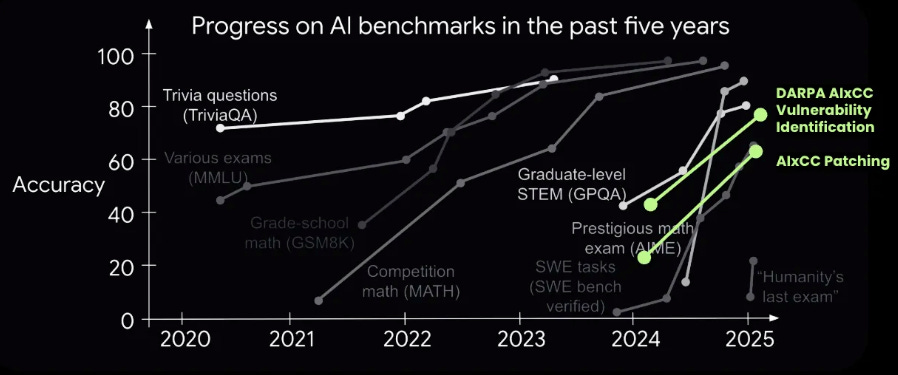
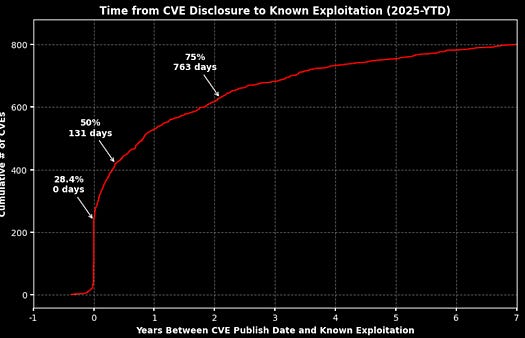
He cites a quote from OpenAI’s Jason Wei which states “The ease of training AI to solve a task is proportional to how verifiable that task is”. This is in part why we continue to see AI, LLMs and Agents scale massively in terms of benchmark scoring at CtFs and other binary activities that have clear verifiable measures of success. As we all know in cyber defense, things are far murky and opaque. His blog provided the below images: As Sergej lays out, until cyber defenders address the verifiability gap and challenges, offense use of AI is likely to far outpace defenses success, which is a very troubling projection, given how defenders already struggle. However, as Sergej noted in his blog:
Sergej does go on to stress that the key here is coupling LLM’s and Agents and proper tool scaffolding, and showed two examples: AppSecMITRE Releases 2025 CWE Top 25Every year, similar to other industry AppSec resources, MITRE updates their “CWE Top 25”, which are the Top 25 Common Weaknesses and Enumerations (CWE). This represents:
MITRE and Cybersecurity and Infrastructure Security Agency recently shared the 2025 CWE Top 2025. Below are some quick takeaways. ↳ XSS continues to dominate the top spot ↳Missing Authorization jumped 5 positions to Number 4. This is defined as “The product does not perform an authorization check when an actor attempts to access a resource or perform an action.” There’s strong parallels here with the recent update of the OWASP Top 10, which has Broken Access Control (#1) and Authentication Failures (#7). So despite the past several years of industry hype around Zero Trust, we seem to be not doing so hot there, and Agents are poised to exacerbate these fundamental problems at-scale. The CWE Top 25 is a great resource for defenders to prioritize and target high priority vulnerabilities, as well as for vendors to potentially due the same, driving Secure-by-Design architectural, design and development decisions. Fixing the Broken Vulnerability Management SystemIn this episode I got to hangout with my friend and Vulnerability Researcher Patrick Garrity 👾🛹💙 of VulnCheck to do a roundup of the latest trends, analysis and insights into the vulnerability and exploitation ecosystem throughout the past year.  We covered a lot of great topics, including:
Rethinking AppSec for AI-Driven Applications I recently had a chance to join Fred Sass and the Security Compass crew for a wide ranging discussion on all things AI and AppSec. We covered topics such as:
And much more. This was a fun conversation, and we tried to cover a lot of ground. Resilient Cyber is free today. But if you enjoyed this post, you can tell Resilient Cyber that their writing is valuable by pledging a future subscription. You won't be charged unless they enable payments. |
Similar newsletters
There are other similar shared emails that you might be interested in: