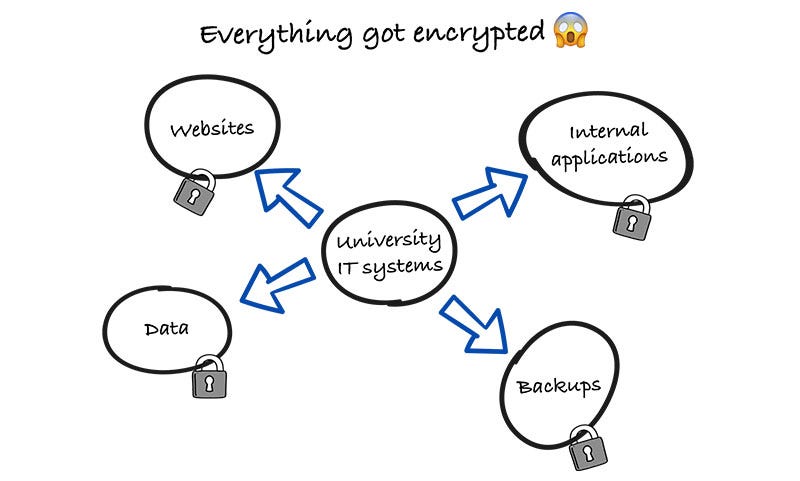
The whole University IT system stopped working 😱
- Gregor Ojstersek and Akash Mukherjee from Engineering Leadership <gregorojstersek@substack.com>
- Hidden Recipient <hidden@emailshot.io>
The whole University IT system stopped working 😱What to do now and how to prevent this from happening in the future?Let AI document your team’s work (Sponsored)There’s an AI tool that creates how-to videos in a very simple way, it’s called Guidde and the reasons why it’s great to use:
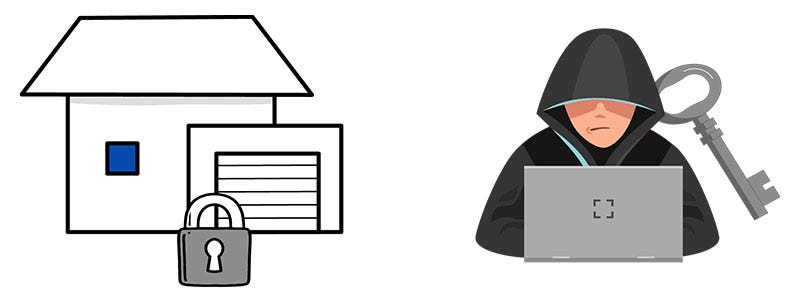
I’ve checked it out and I really like how simple it is to use and how fast you can generate an explainer video ready to share. Try Guidde for free: Let’s get back to this week’s thought. IntroAs some of you may know, I am from Slovenia and Maribor is where I grew up. In today’s article, we’ll go through a recent cyberattack that happened to the University of Maribor. The goal of the article is to help as many people and organizations to prevent such attacks in the future and also what to do in case you get attacked. To ensure we’ll get the best insights, I’ve teamed up with Akash Mukherjee. Akash is the author of the book: “The Complete Guide to Defense in Depth: Learn to identify, mitigate, and prevent cyber threats with a dynamic, layered defense approach” He has broad experience in security, penetration testing and designing secure systems. His recent endeavors include working as a Security Lead for Google and Apple. Let’s get straight into it! The cyberattack on the University of Maribor happened last monthBased on 24ur, a local Slovenian news portal, there was a cyberattack last month on the University of Maribor in Slovenia. The result of the attack? All the websites, data, including the backups and IT systems got encrypted and are no longer available to use. That means that all of the data may not be available to the students or may not even be recovered. It was a ransomware attack called “babuk ransomware” which was connected with the 2021 attack on Washington’s police department, where a lot of sensitive information was stolen. Let’s define what exactly ransomware is. What is ransomware?Ransomware is a type of malicious software (malware) designed to deny users or organizations access to their computer files by encrypting them and demanding a ransom payment for the decryption key. This type of cyberattack has become the most prominent in recent years and has affected various of different companies, individuals and also highly critical infrastructures like banks, hospitals and universities. Did you know there are several types of ransomware available? Based on Crowdstrike, there are 5 main types of ransomware: 1. Crypto Ransomware or Encryptors Encryptors are one of the most well-known and damaging variants. This type encrypts the files and data within a system, making the content inaccessible without a decryption key. 2. Lockers Lockers completely lock you out of your system, so your files and applications are inaccessible. A lock screen displays the ransom demand, possibly with a countdown clock to increase urgency and drive victims to act. 3. Scareware Scareware is fake software that claims to have detected a virus or other issue on your computer and directs you to pay to resolve the problem. Some types of scareware lock the computer, while others simply flood the screen with pop-up alerts without actually damaging files. 4. Doxware or Leakware Leakware threatens to distribute sensitive personal or company information online, and many people panic and pay the ransom to prevent private data from falling into the wrong hands or entering the public domain. 5. RaaS (Ransomware as a Service) Ransomware as a Service (RaaS) refers to malware hosted anonymously by a “professional” hacker that handles all aspects of the attack, from distributing ransomware to collecting payments and restoring access, in return for a cut of the payment. Now that we defined the attack and what ransomware is + different types, let’s get into how to prevent it! Akash, over to you. Preventing ransomwareWho’s using paper trail to run organizations today? Nobody! This increased reliance on digital assets put extra pressure on traditional industries like hospitals, education to proactively protect their data. The fundamental concept behind ransomware attacks is an attacker holding the only key to your house. They will return the key to you, if you pay them money. As you visualize this scenario, there are two things you can do,
In the world of cybersecurity, it’s not much different. Ransomware attacks take advantage of the weaknesses in edge devices to plant malicious software.
This characteristic makes ransomware relatively easy to build. No organization is safe from the threat of ransomware, but it’s simple to protect against them. Let’s go over some common defenses: 1. Create BackupsMost ransomware victims are forced to pay because they didn’t have a copy of their critical data. As ransomware became prevalent, having backups is a necessary tool for disaster recovery. 2. Educate UsersThe most common way of delivering ransomware is by phishing users. Attackers send emails to target individuals and have their malware delivered into a corporate network. It’s important to counter attacks with technical controls, but security awareness in internal users remains a central piece of the puzzle. 3. Update SoftwareIn the last couple of years, we have seen increasing supply chain security problems. Malware inserted into the open-source dependencies you use daily has become a common path. It’s important to keep dependencies up-to-date to avoid having open doors to your castle.
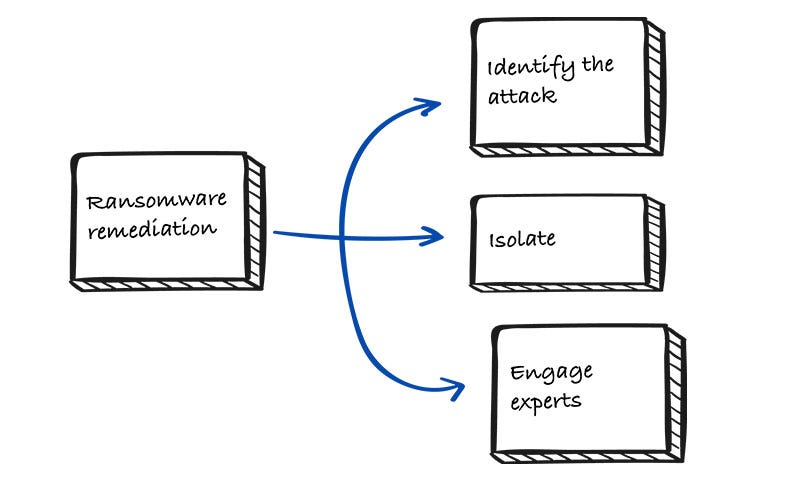
Did you know 50% of ransomware victims who pay the ransom don’t get their data back? So what do you do after getting impacted? Steps towards remediation from a ransomware attackThere’s a saying in security, nothing is 100% secure. In case you find yourself in a situation where the attacker not only encrypts your data but threatens to leak confidential information (ransomware 2.0), here’s what you need to do: Identify the attackActing under duress can impact negatively. Panicking after getting a ransom note can be devastating, but it’s important to assess the impact of an attack first. Look for the following signs in different components of your network:
IsolateOnce you have drawn a clear boundary of impacted systems, it is important to take them out of the network. Don’t power off unless absolutely necessary.
Here are a few things you should do:
One way to make this better is to design a kill-switch script that takes out parts of systems from the network easily. Engage expertsOnce the attack is isolated, the next step is to start remediation. Engaging experts from inside or outside your organization is important. Below are the three personnel to involve at this point:
The right experts can sometimes help recover the files and identify the attacker. Useful leads in the investigation will result in faster resolution. If your organization gets attacked, the instinct might be to pay the ransom to avoid external scrutiny and public embarrassment.
Don’t pay the ransom. Key takeawaysGregor here again. Here are the main key takeaways from Akash’s insights:
Last wordsSpecial thanks to Akash for sharing his insights on this very important topic! Make sure to follow him on LinkedIn. If you’d like to read more about how to prevent or remediate such attacks, I’d recommend checking out his book The Complete Guide to Defense in Depth. We are not over yet! I had a great time at the Infoshare conference in Katowice, Poland.I gave a talk: Stop learning programming languages and start building credibility. Also met with Michał Poczwardowski, a fellow newsletter writer. He writes the Perspectiveship newsletter. BrandGhostMy friend Nick Cosentino built a creator tool that makes it easy to post on various different social platforms at the same time. If you’re posting on social media, that might be a great tool for you! You can try out the free version or you can get it for 30% off via Black Friday discount code: BLKFRI30. Take a look at it here. Liked this article? Make sure to 💙 click the like button. Feedback or addition? Make sure to 💬 comment. Know someone that would find this helpful? Make sure to 🔁 share this post. Whenever you are ready, here is how I can help you further
Get in touchYou can find me on LinkedIn or Twitter. If you wish to make a request on particular topic you would like to read, you can send me an email to info@gregorojstersek.com. This newsletter is funded by paid subscriptions from readers like yourself. If you aren’t already, consider becoming a paid subscriber to receive the full experience! You are more than welcome to find whatever interests you here and try it out in your particular case. Let me know how it went! Topics are normally about all things engineering related, leadership, management, developing scalable products, building teams etc. Invite your friends and earn rewardsIf you enjoy Engineering Leadership, share it with your friends and earn rewards when they subscribe. |
Similar newsletters
There are other similar shared emails that you might be interested in: