A Fake Tech Company Scam: Here's How I Caught It in Time
- Gregor Ojstersek and Kjartan Manvelyan from Engineering Leadership <gregorojstersek@substack.com>
- Hidden Recipient <hidden@emailshot.io>
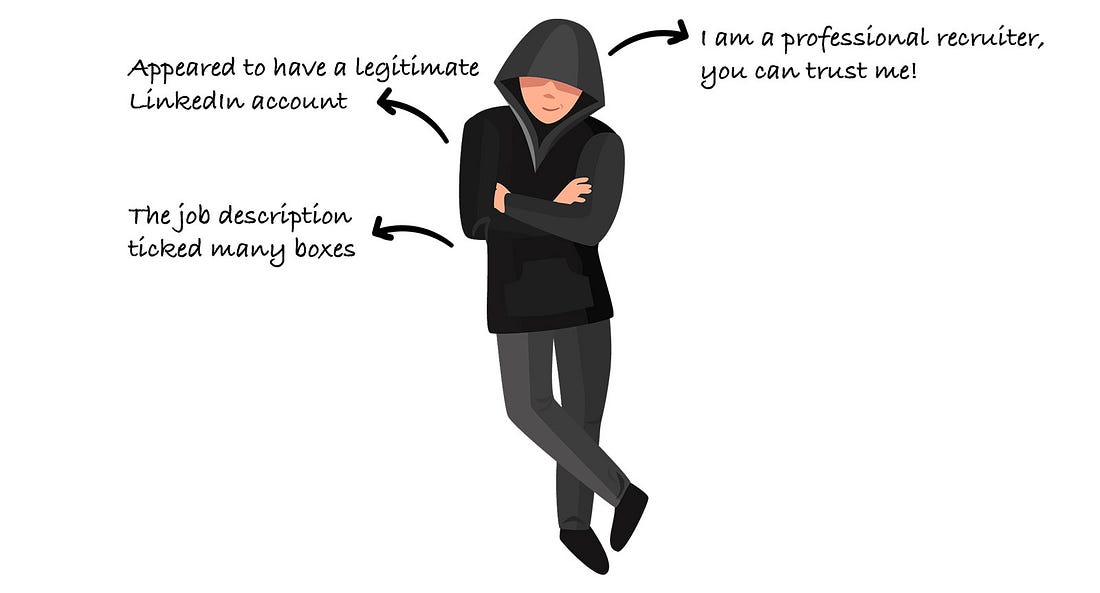
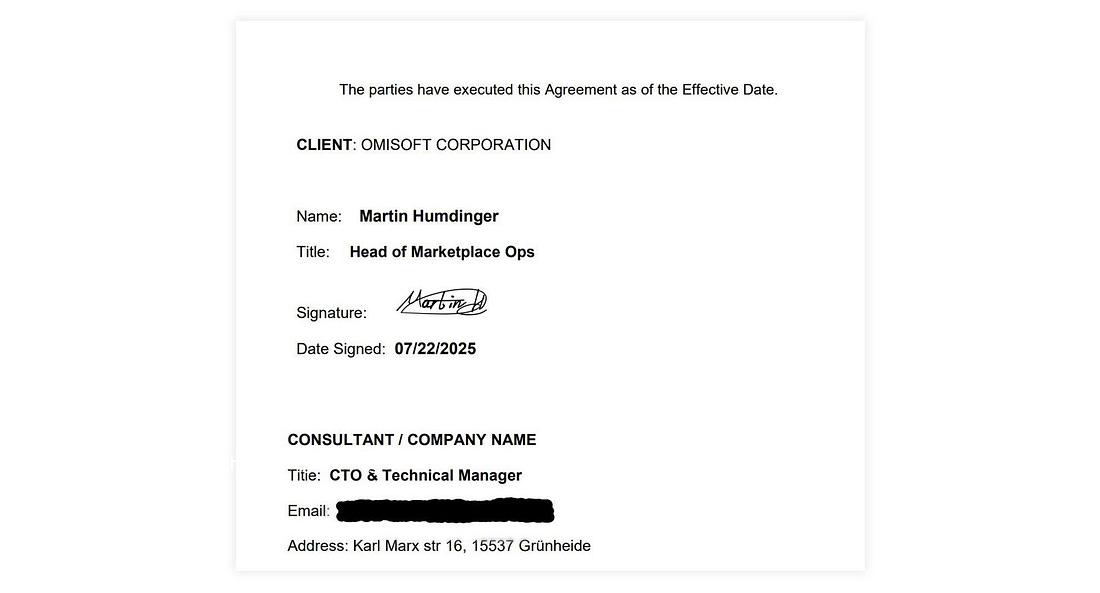
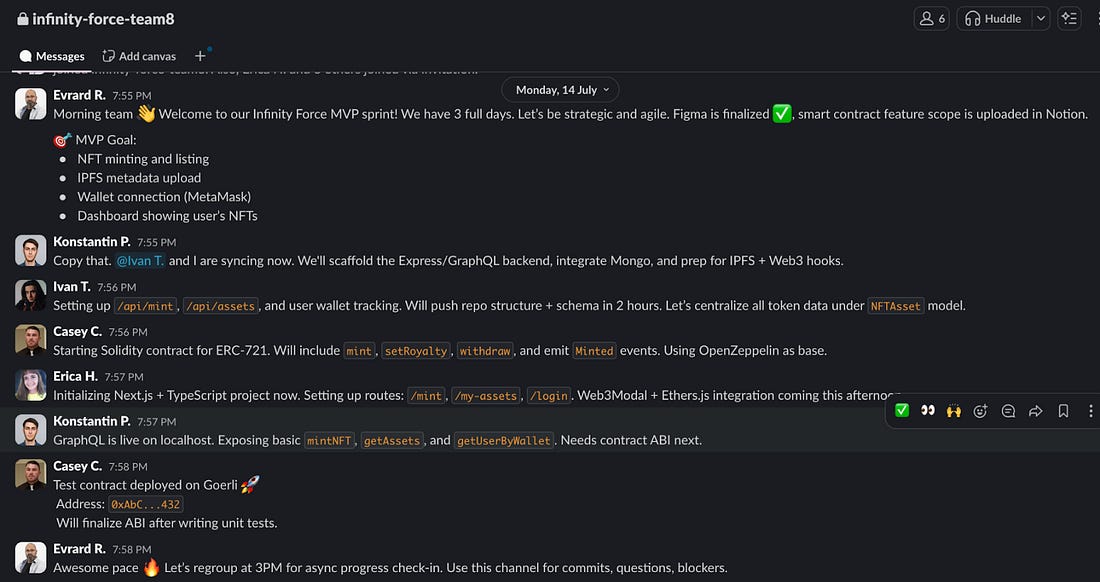
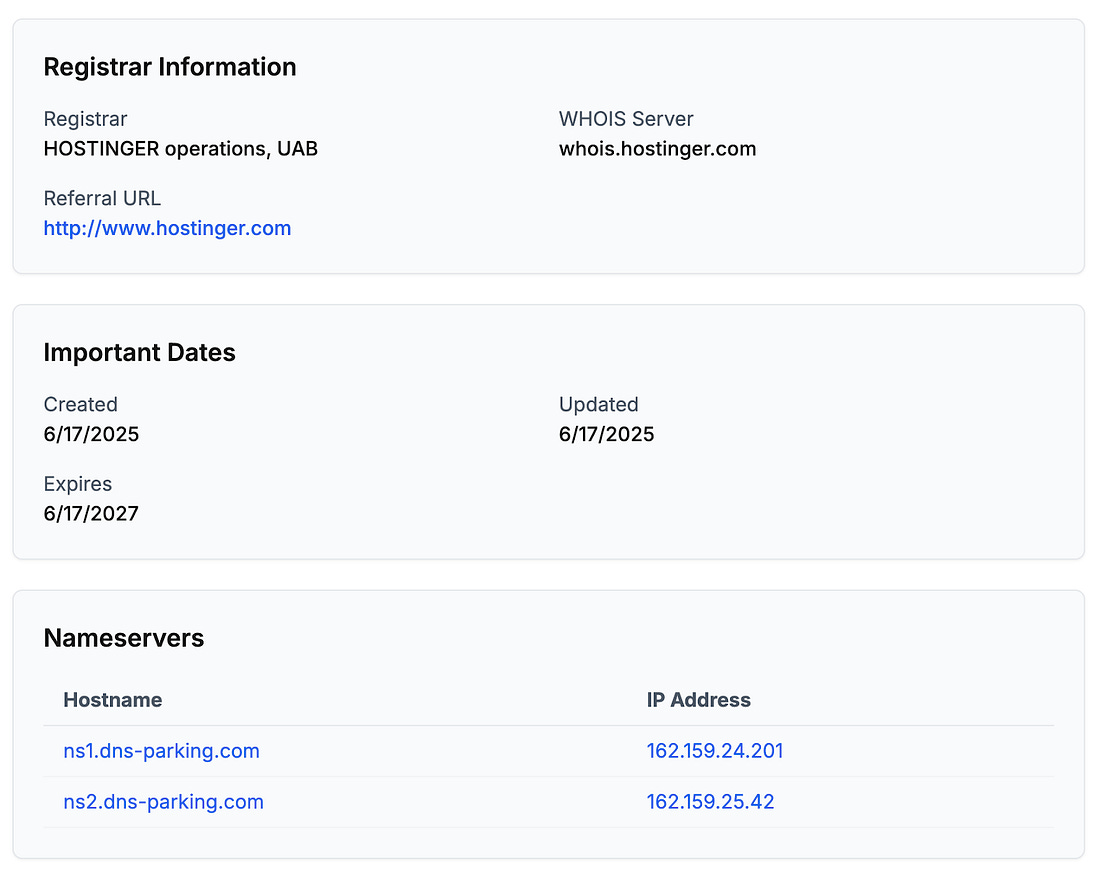
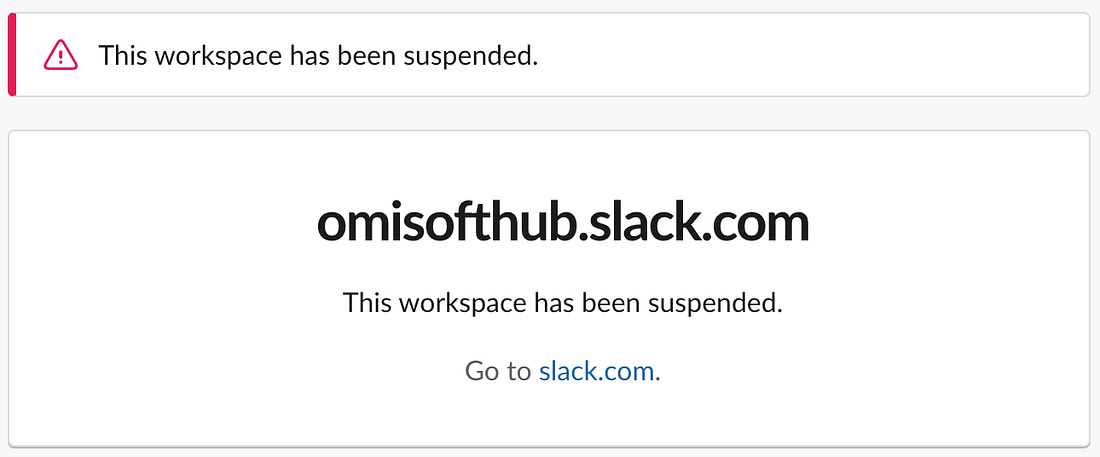
Hey, Gregor here 👋 This is a free edition of the Engineering Leadership newsletter. Every week, I share 2 articles → Wednesday’s paid edition and Sunday’s free edition, with a goal to make you a great engineering leader! Consider upgrading your account for the full experience here. A Fake Tech Company Scam: Here's How I Caught It in TimeA sophisticated scam where they offered a role to an experienced tech professional with the intention of stealing his crypto wallet credentials!This newsletter is sponsored by DevStats. Out Ship, Out Deliver, Out Perform. DevStats helps engineering leaders unpack metrics, experience flow, and ship faster so every release drives real business impact. ✅ Spot bottlenecks before they stall delivery It’s time to ship more and make your impact impossible to ignore. Thanks to DevStats for sponsoring this newsletter. Let’s get back to this week’s thought. IntroWith the rise of AI, there are not just upsides but also downsides. We have seen AI cheating in interviewees, where interviewees actually change their appearance with AI and respond to questions with answers generated by ChatGPT. If you’re interested in how to design your interview process against it, check this article: We have also seen a rise of various different scams, some including deepfakes impersonating people, enhanced cyber attacks and various automated phishing attacks. This story that we are going to go through today is particularly relevant for all tech professionals searching for new roles. First of all, be careful and make sure to spot the red flags as soon as possible. There are many fake companies out there with fake roles, looking to benefit from people who are eager to contribute, so make sure to be careful. Kjartan Manvelyan was hired for a role of technical project manager, but then it turned out that everything was fake: the people, the Slack workspace, the codebase. All with the intention for him to download the codebase so they could do harmful things. Luckily, he found out at the right time, so no harmful things have happened. And to make it worse, all of this happened on his birthday! To ensure that this doesn’t happen to you and that you’ll be well-prepared if something similar occurs, Kjartan has kindly shared his experience in detail with us. Make sure to read on. Introducing Kjartan ManvelyanKjartan Manvelyan is a Fractional CTO and a seasoned tech professional. He specializes in driving impactful results across technology, team leadership, and cloud automation. Kjartan is currently in search of a new role, so make sure to contact him while he is still available. But please, no scams! The Sophisticated ScamAs someone who has worked as a Fractional CTO and consultant with various startups and clients across Europe for the past six years, I thought I had seen it all when it came to phishing attacks disguised as real jobs. But nothing quite prepared me for the sophisticated scam that almost caught me on what was supposed to be the start of an exciting new role — and on my birthday, no less. As I mentioned, this wasn't my first encounter with malicious job offers. Over the years, I've been targeted by several fake interview schemes, but this one stood out for its next-level sophistication. The scammers had clearly refined their approach over many iterations. This was not their first rodeo. Initial Contact With RecruiterThe first red flag I should have caught was how the initial contact happened. The "recruiter" presented themselves professionally, with what appeared to be a legitimate LinkedIn profile. They spoke about a freelance role as a technical project manager in a well-funded blockchain project, a role I am qualified for and which happens to be on the current list of titles in my job search. The job description ticked many boxes; it aligned with my background in engineering leadership, offered great compensation, and seemed like a natural fit for my skill set. And it was remote. However, looking back, there were subtle warning signs I should have picked up on earlier. The recruiter was vague about the specific company details during our initial conversations. I checked out the company website, which seemed legit. It was a blockchain development agency based in Estonia and Ukraine, named Omisoft. I looked them up for due diligence and verified that they were the real deal. I also performed a WHOIS lookup on their domain name to check that it hadn’t been recently registered, as well as finding out who potentially owned the domain. This protects me from any potential phishing attempt, and also hides my real IP, as Tails OS is a Linux distro built to be anonymous. The first time I managed to type the URL incorrectly, which took me to a site that had no https certificate. When I asked the recruiter about this, expressing that a missing certificate was concerning to me and if they could explain it, they corrected me and gave me the link again. In my previous encounters with fake interviews, the scammers made the mistake of moving too quickly to the technical assessment phase, often asking me to download and run code within the first or second interaction. It could be a Bitbucket or GitHub private repository - in the most amateur cases, a Zip file. The malicious code would be obfuscated, basically, how AI slop code can look like. Imagine strangely named variables and code that, in general, is difficult to understand at first. After a more thorough inspection, it becomes evident that the intent is malicious, and that the only thing the code does is to steal your crypto wallet credentials and saved passwords. It can also be embedded in a web application that looks real at first, or in an installation script. Video Interview With Sam, the Hiring ManagerAfter the initial chat with the recruiter on LinkedIn, next up was a call with Sam, the supposed hiring manager. The recruiter gave me a Calendly link, which is also something I have never seen used by scammers before. However, by now my internal alarms had already been raised multiple times, so at this point I decided to play along till the end to see where this journey would take me. This was going to be interesting. When our call first connected, I was surprised to see “Sam” on video in front of me, looking exactly like the photo from his Gmail account. However, the video was choppy, and within a few seconds, he asked to switch to audio-only, as “there seems to be connection problems”. Potentially believable, as I am sure most of us have experienced having to do the same on some video calls. This is what makes most sense, as it’s very unlikely Sam was using some form of network speed throttling to simulate a poor connection while actually showing his real face on camera. I proceed on to the interview, feeling excited to get the chance to talk to a scammer for a whole half hour. Add a strong Russian/Ukrainian accent on top. I am sure he has done this many times, and figured I would be bored as well. At this point, I feel some empathy for the guy. Sam sounds tired. After going through many questions and elaborating more on my resume and experience, he seems satisfied. My feeling at the end of his questions was that I had passed their requirements. They were definitely looking for someone with technical skills. After a few days, they reached out with good news: they wanted to hire me. The timeline felt kind of reasonable, not rushed like in my previous experiences. Phishing information for NDASam proceeds to ask me for the information needed for the NDA. They want to know a lot about me - phone number, birthdate, address, citizenship, the works. I politely reply that I will not be providing my birthdate and some other info, as this has never been necessary previously in my career after signing many NDAs. The document looked professional at first glance, with proper formatting and legal language, but again, I was asked to fill out my birth date and other sensitive information. The document is signed by “Martin Humdinger, Head of Marketplace Ops”. Below is a screenshot, along with the fake address I provided. I proceed to Google the mysterious Martin Humdinger. Nothing comes up. The name didn't match any LinkedIn profiles or other online presence associated with the company. The Fake SlackAt first glance, the workspace looked convincing. There were approximately a dozen team members with kind of realistic-looking profiles, and what appeared to be a chat between a project manager and his team, who responded with status updates on their progress. As I spent another moment to actually read the conversation, it got crazy pretty quickly. The developers were responding to their manager with superhuman speed. Replies came within seconds or a minute or two, which simply doesn't happen in real work environments. Even in the most effective teams I've worked with, people need time to context-switch, think through problems, actually solve the problems, and then come up with meaningful responses. Here, you had what looks like an almost complete MVP, pretty much done in 3 minutes! Even more telling was the language quality. Every message was written in perfect English with flawless grammar, short and efficient sentences that all shared the same style, and sophisticated punctuation like em dashes, which often is a tell that someone is using an LLM. In my career of working with engineering teams, I've never seen such consistently perfect communication. Real workplace Slack channels are filled with typos, incomplete thoughts, emoji reactions, and probably some bad memes here and there. The content itself felt artificial. Conversations lacked the organic flow of real team discussions. There were no inside jokes, no references to shared experiences, no technical problems people struggled with. It read like someone had prompted an AI with "create a Slack conversation simulating blockchain engineers answering their project manager". Another observation: I also noticed a team member who had a company email listed in their bio: omisofthub.net As one can see, the domain was registered in June. It was clear the scammers are not affiliated with omisoft.net - otherwise they would have used that domain.
I did not attempt to send an email to the listed address or chat with the AI team members. I did, however, get a response from Sam to my questions regarding the contract. The larger patternI would consider this relatively sophisticated attempt the culmination of the previously mentioned experiences. Back then, the scammers made silly mistakes that made them easier to catch: Moving too fast: Earlier scams rushed to the technical assessment phase, often asking me to download and run code within the first conversation. This latest attempt was more patient, building credibility over multiple interactions. I even had to remind them to send the Slack invitation, as I still hadn’t received it the day before my work was supposed to begin. It could be that they were too busy, but I’d like to think this was intentional. No professional recruitment: Previous attempts skipped professional recruiters entirely, and would instead present themselves as entrepreneurs/co-founders. This time, they invested in creating a more convincing recruitment experience. Lack of detail: Earlier attacks provided vague job descriptions and couldn't answer specific questions about the company structure or their technical challenges. While this latest attempt was still light on details, they had improved their responses. The short interview with the hiring manager did not give me enough time to gain deep insights about the project. Red Flags To Look ForBased on what I learned so far, here are the warning signs that should raise immediate concerns: Recruitment red flags:
Interview warning signs:
Documentation issues:
Communication patterns:
Protective MeasuresThe cybersecurity principles that protected me can help others avoid similar situations: Always use sandboxed environments If you must run unknown code or visit suspicious links, do so in isolated virtual machines that can't access your main systems or sensitive data. I recommend Tails OS in a VM or on a Live USB stick booted up on an old laptop you have lying around. Kali Linux works too, but make sure you are connected through Tor before you open any links. You don’t want to reveal your IP to the attacker. Verify company information Research tax ID numbers, business addresses, and listed employees through search engines and professional networks. Trust your intuition If communication patterns feel artificial or responses seem too perfect, investigate further before proceeding. Ask specific questions Legitimate companies can provide concrete details about their technical challenges, team structure, and business operations. Take time for due diligence Don't let urgency pressure you into skipping verification steps, especially for attractive opportunities. The Evolution of Tech ScamsWhat made this latest attempt particularly concerning was its sophistication. The scammers had clearly studied previous failed attempts and refined their approach. They understood that engineers are naturally suspicious of rushing to download and run an unknown codebase, so they built a more elaborate setup to establish credibility first. The attackers know people with blockchain experience often have valuable digital assets and access credentials worth targeting. Unfortunately for the attackers in this particular case, I am too paranoid a person to keep any crypto credentials on my pc. That’s what we have hardware wallets for. As these operations become more advanced, separating fake interactions from real ones will become increasingly challenging over the next years, and I also predict we will see the same level of complexity in job recruitment scams across all industries. Verify First, Trust After ConfirmationWhile this experience was both scary and deeply fascinating to be part of, it shows how dangerous the current scams out there have become - and has convinced me society should brace for an impending impact. Soon, these operations will be fine-tuned and fully tailored to the individual target, making it almost impossible to detect in time. Job seekers should tread carefully and educate themselves on basic cybersecurity principles before starting their job hunt. The cybersecurity mindset that has served me well throughout my career — verify first, trust after confirmation, proved essential in avoiding what could have been a significant security breach. By sharing these experiences and warning signs, I hope to help others evade similar threats. Remember: if something feels off, it probably is.
Your future self will thank you for the caution. Still looking for that legitimate new role, by the way. But I'll definitely be keeping my guard up if you want to schedule an interview. Last wordsSpecial thanks to Kjartan for sharing this story with us! Make sure to check him out on LinkedIn and also if you’re team/company is looking to hire a person with a broad skillset, such as Kjartan’s, definitely contact him, but as I mentioned above, no scams! We are not over yet! Not Communicating Your Impact is Killing Your Career as an EngineerI’ve seen countless engineers doing great work, but afraid to come across as if they are “bragging” or “selling”. But then, when it’s time to announce the next promotion, they get overlooked. Learn how to communicate your impact in this video.  New video every Sunday. Subscribe to not miss it here: Liked this article? Make sure to 💙 click the like button. Feedback or addition? Make sure to 💬 comment. Know someone that would find this helpful? Make sure to 🔁 share this post. Whenever you are ready, here is how I can help you further
Get in touchYou can find me on LinkedIn, X, YouTube, Bluesky, Instagram or Threads. If you wish to make a request on particular topic you would like to read, you can send me an email to info@gregorojstersek.com. This newsletter is funded by paid subscriptions from readers like yourself. If you aren’t already, consider becoming a paid subscriber to receive the full experience! You are more than welcome to find whatever interests you here and try it out in your particular case. Let me know how it went! Topics are normally about all things engineering related, leadership, management, developing scalable products, building teams etc. Invite your friends and earn rewardsIf you enjoy Engineering Leadership, share it with your friends and earn rewards when they subscribe. |
Similar newsletters
There are other similar shared emails that you might be interested in: